资讯类
苹果已发布macOS High Sierra 10.13.1创建root用户漏洞的补丁,建议用户赶紧升级!
Apple closes that big root hole – “Install this update as soon as possible”
https://support.apple.com/en-us/HT208315
malwarebytes对此漏洞的介绍
objective-see对此漏洞进行源码级别的分析
https://objective-see.com/blog/blog_0x24.html
浏览器被关闭后挖矿脚本竟然还在运行!
技术类
malwarebytes对持久型浏览器挖矿脚本(关闭浏览器之后挖矿还在进行)的分析
Persistent drive-by cryptomining coming to a browser near you
巴西的WannaPeace勒索软件样本,该样本只会加密C://testes 目录
https://twitter.com/malwrhunterteam/status/935847705510924288
https://www.virustotal.com/en/file/653bc2b16b1624e045c1225810185e9aa3694dc378fe0095e2052b7f1e265d01/analysis/1511955717/
新的网页浏览安全工具:DNS over TLS
https://news.hitb.org/content/new-web-browsing-security-tool-arrives-dns-over-tls
使用Shodan的ssh公钥扫描器
https://github.com/0x27/ssh_keyscanner
Win32k NtUserOpenDesktop拒绝服务漏洞(9200-17046)
https://gist.github.com/hfiref0x/6e726b352da7642fc5b84bf6ebce0007
Ursnif变种使用thread local storage(TLS)callbacks进行进程注入
https://www.fireeye.com/blog/threat-research/2017/11/ursnif-variant-malicious-tls-callback-technique.html
Cisco Talos的研究员分析了最新版本的ROKRAT
http://blog.talosintelligence.com/2017/11/ROKRAT-Reloaded.html
exploit-db的官方github仓库
https://github.com/offensive-security/exploit-database
Linux平台systemd漏洞导致的拒绝服务
利用frida的新型Arm64Writer API来构建内存中的反向TCP shell
https://versprite.com/og/frida-engage-part2/index.html
pfSense 2.3.1_1 远程命令执行
https://cxsecurity.com/issue/WLB-2017110154
盘点2017年WordPress插件的漏洞
https://blog.ripstech.com/2017/wordpress-plugin-vulnerabilities-static-analysis/
WordPress Plugin Code Scanner
http://www.kitploit.com/2017/11/wpsploit-wordpress-plugin-code-scanner.html
https://github.com/m4ll0k/WPSploit
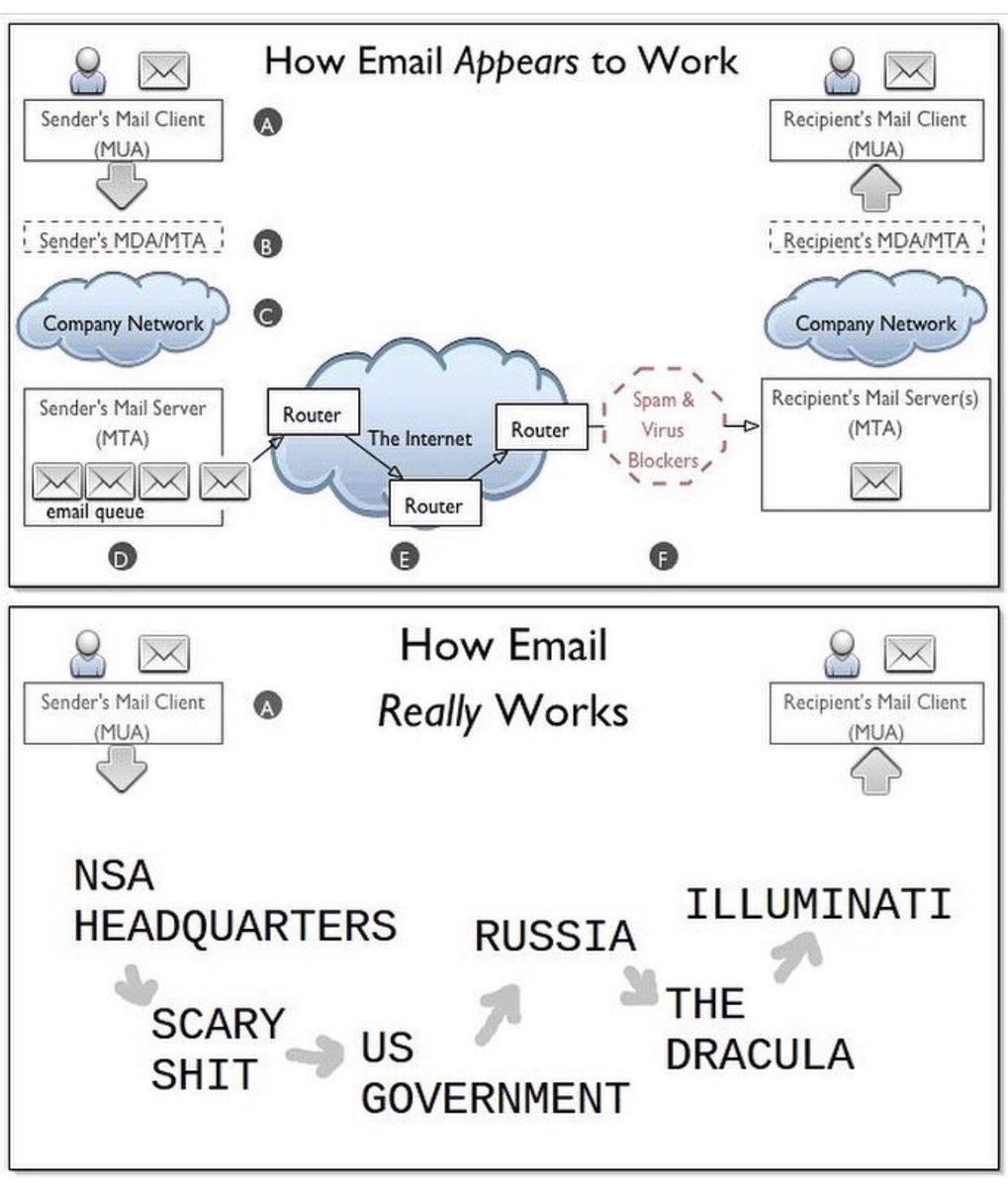
Email是如何运转的