热点概要:CVE-2017-15670, CVE-2017-15671 glibc在glob.c的堆溢出、CVE-2017-5133: Google Chrome PDFium TIFF off-by-one读/写漏洞(可导致命令执行和信息泄露)、看我如何一步一步发现TP-Link路由器的远程代码执行(CVE-2017-13772)、验证Zimperium移动端机器学习恶意软件检测的结果、如何通过USB完全接管系统
资讯类:
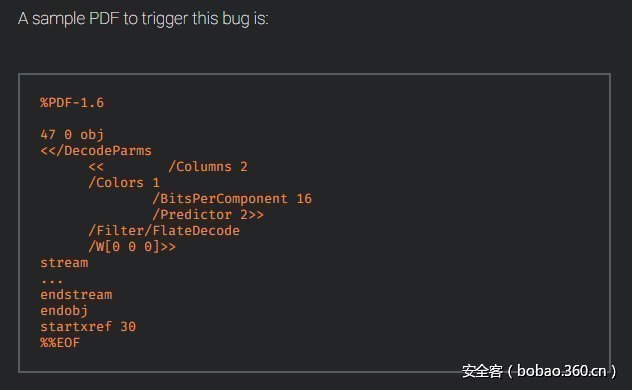
CVE-2017-15670, CVE-2017-15671 glibc在glob.c的堆溢出
http://seclists.org/oss-sec/2017/q4/119
加拿大间谍机构发布其网络防御工具
https://www.hackread.com/canadas-spy-agency-releases-its-cyber-defense-tool-for-public/
技术类:
如何通过USB完全接管系统
http://blog.ptsecurity.com/2017/10/how-to-obtaining-full-system-access-via.html
CVE-2017-5133: Google Chrome PDFium TIFF off-by-one读/写漏洞(可导致命令执行和信息泄露)
(影响范围 Google Chrome <= 60.0.3112.101
漏洞存在于Chrome的Pdfium TIFF图像解码功能,可由victim在Chrome中打开恶意构造的PDF文件触发)
https://www.talosintelligence.com/reports/TALOS-2017-0432
验证Zimperium移动端机器学习恶意软件检测的结果
https://blog.zimperium.com/validating-machine-learning-detection-mobile-malware/
The First PS4 Kernel Exploit: Adieu
https://fail0verflow.com/blog/2017/ps4-namedobj-exploit/
看我如何一步一步发现TP-Link路由器的远程代码执行(CVE-2017-13772)
https://www.fidusinfosec.com/tp-link-remote-code-execution-cve-2017-13772/
Hack the BTRSys1 VM (Boot2Root Challenge)
http://www.hackingarticles.in/hack-btrsys1-vm-boot2root-challenge/
Seccubus:简易自动漏洞扫描、报告、分析工具(可结合Nessus、OpenVAS、Nikto、NMap等)
http://www.kitploit.com/2017/10/seccubus-easy-automated-vulnerability.html