热点概要:OSX平台Proton后门恶意软件——供应链攻击、Office DDE多种利用方式已公开、俄罗斯网络间谍正抓紧exploit最近Flash的0day、本周勒索软件:Magniber,Hermes,Sage 2.2 ,Tyrant,ViiperWare,Blue Eagle新变种、看我如何发现Yahoo! Guesthouse 的SSRF漏洞的、游戏键盘确实比其他键盘快吗——记一次键盘延迟研究
资讯类:
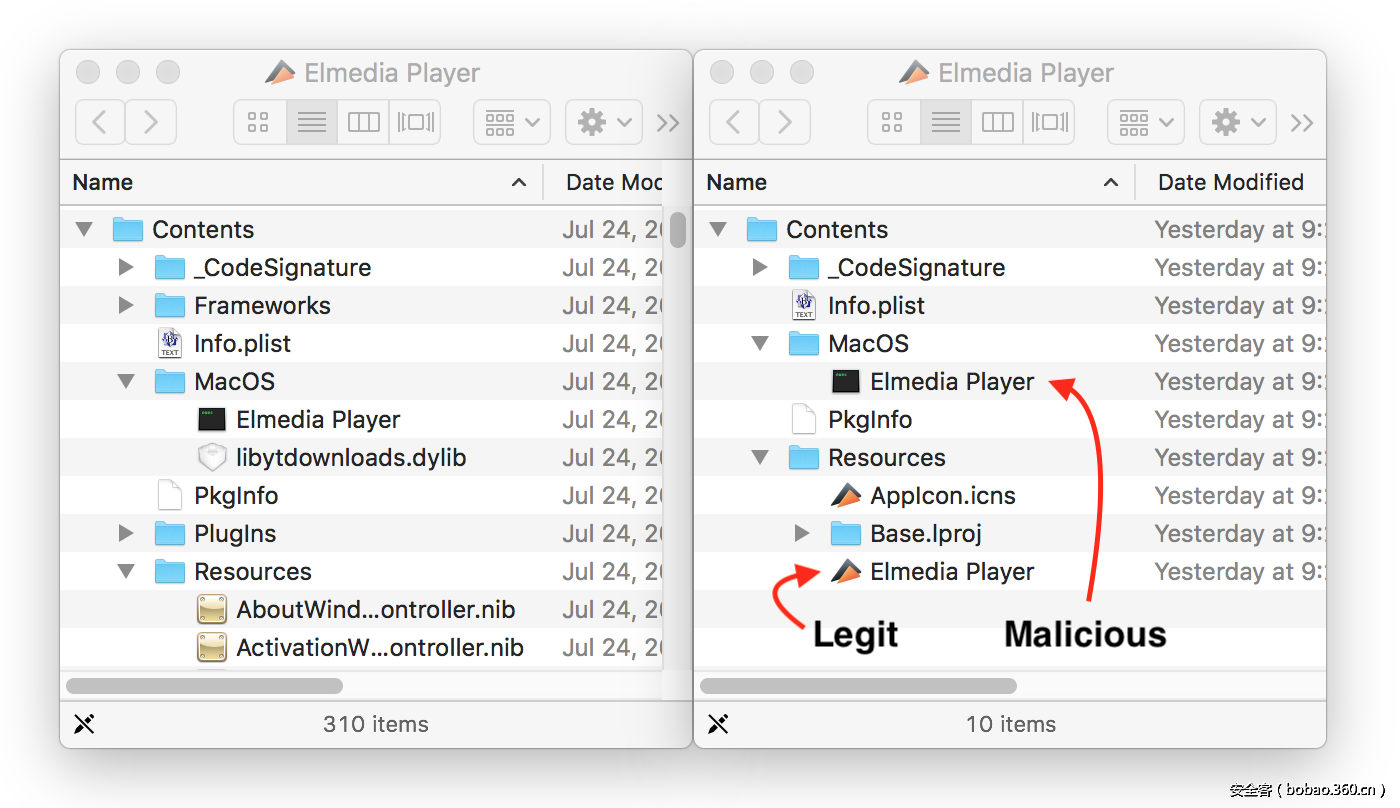
OSX平台Proton后门恶意软件——供应链攻击
(从Eltima官方下载的Elmedia Player播放器居然是恶意软件!)
https://blog.malwarebytes.com/cybercrime/2017/10/mac-malware-osx-proton-strikes-again/
https://www.welivesecurity.com/2017/10/20/osx-proton-supply-chain-attack-elmedia/
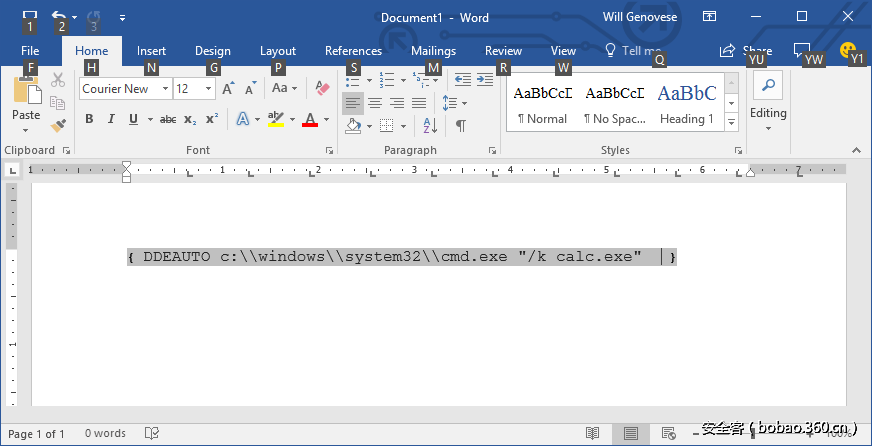
Office DDE多种利用方式已公开(打开outlook客户端查看邮件及office文档时注意不清楚的弹框不要点确认)
http://willgenovese.com/office-ddeauto-attacks/
临时缓解措施,关闭DDEAUTO
https://gist.github.com/wdormann/732bb88d9b5dd5a66c9f1e1498f31a1b
趁热打铁:俄罗斯网络间谍正抓紧exploit最近Flash的0day
中情局负责人称正努力消灭WikiLeaks这样的威胁
http://www.washingtontimes.com/news/2017/oct/20/cia-working-take-down-wikileaks-threat-agency-chie/
本周勒索软件:Magniber,Hermes,Sage 2.2 ,Tyrant,ViiperWare,Blue Eagle新变种
技术类:
游戏键盘确实比其他键盘快吗——记一次键盘延迟研究
http://danluu.com/keyboard-latency/
看我如何发现Yahoo! Guesthouse 的SSRF漏洞
https://medium.com/@th3g3nt3l/how-i-found-an-ssrf-in-yahoo-guesthouse-recon-wins-8722672e41d4
使用NtCreateThreadEx/QueueUserAPC/SetThreadContext/SetWindowsHookEx进行DLL注入
https://github.com/FuzzySecurity/PowerShell-Suite/blob/master/Stage-RemoteDll.ps1
BaRMIe – Java RMI Enumeration And Attack Tool
http://www.kitploit.com/2017/10/barmie-java-rmi-enumeration-and-attack.html
Blazy ——登录爆破工具(同时可检测CSRF, Clickjacking, Cloudflare and WAF)
http://www.kitploit.com/2017/10/blazy-modern-login-bruteforcer-which.html
NSEarch:Nmap脚本搜索引擎
https://n0where.net/nmap-scripting-engine-search-nsearch/
open redirect subdomains scanner
https://github.com/ak1t4/open-redirect-scanner
用法:
./redirect.py [subdomains.file] [redirect-payload]