资讯类
Check Point安全研究员发现APKTool, IntelliJ, Eclipse, and Android Studio这些工具中用于XML解析的库存在XXE漏洞,安卓应用也可能会受到攻击
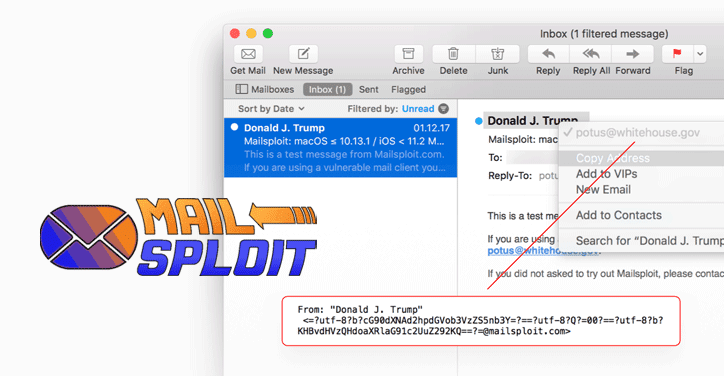
Mailsploit:影响超过30个流行邮件客户端的漏洞集合,可被利用作包括远程代码执行、邮件欺诈攻击等
https://thehackernews.com/2017/12/email-spoofing-client.html
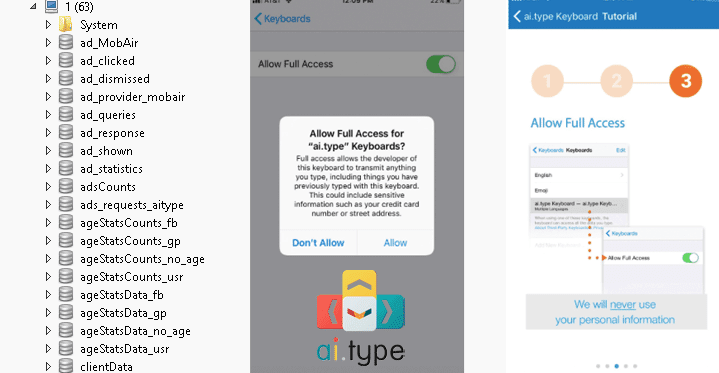
Ai.type不慎泄露3100万用户的个人数据,信息详细程度令人咋舌
https://thehackernews.com/2017/12/keyboard-data-breach.html
技术类
JavaScript – Web Assembly V8 WASM RCE漏洞
https://bugs.chromium.org/p/chromium/issues/detail?id=759624
门罗币I2NP消息处理中潜在的缓冲区溢出漏洞
https://hackerone.com/reports/291489
Badintent的安装与配置
http://blog.obscuritylabs.com/badintent-setup/
Mirai变种Sotari预警
Parsedroid漏洞分析
https://research.checkpoint.com/parsedroid-targeting-android-development-research-community/
WARBIRD与Windows 10 privesc内核利用实例
https://blog.xpnsec.com/windows-warbird-privesc/
Cookie中的新属性Samesite介绍
https://medium.com/compass-security/samesite-cookie-attribute-33b3bfeaeb95
Event Viewer UAC Bypass PoC
https://ghostbin.com/paste/7zccf
Windows日志监控与ELK集成的故事
Mailsploit:邮件客户端潜藏的危险
https://www.mailsploit.com/index
图形化思考——使用Timesketch探索数据
https://medium.com/timesketch/thinking-in-graphs-exploring-with-timesketch-84b79aecd8a6
RSA如何工作?溯源TLS
https://fly.io/articles/how-rsa-works-tls-foundations/
Dridex归来!Necurs僵尸网络分发恶意软件
http://malware-traffic-analysis.net/2017/12/04/index2.html
深入解密HC7