热点概要:Samsung SRN-1670D网络录像机的Web Viewer 1.0.0.193版本任意文件上传漏洞、AVGater:新的漏洞利用反病毒软件安装恶意软件、微软研究人员利用机器学习和深度神经网络发现软件安全漏洞、Google邮件通知安卓app开发者将那些滥用“无障碍”服务的app从Play Store中移除、视频会议系统Polycom HDX的远程命令执行
资讯类:
Samsung SRN-1670D网络视频录像机的Web Viewer 1.0.0.193版本任意文件上传漏洞
https://www.exploit-db.com/exploits/43138/
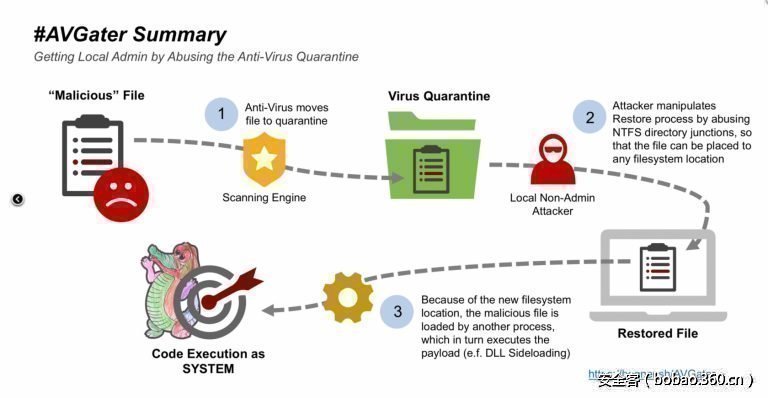
AVGater:新的漏洞利用反病毒程序安装恶意软件
https://www.hackread.com/new-vulnerability-exploits-antivirus-programs-to-install-malware/
微软研究人员利用机器学习和深度神经网络发现软件安全漏洞
https://www.microsoft.com/en-us/research/blog/neural-fuzzing/
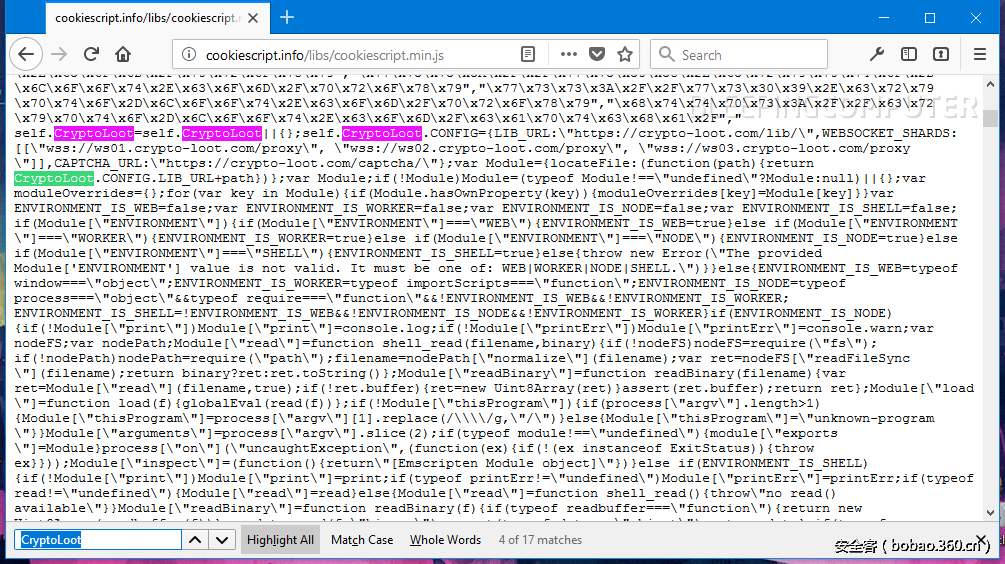
同意Cookie的弹窗释放浏览器挖矿脚本
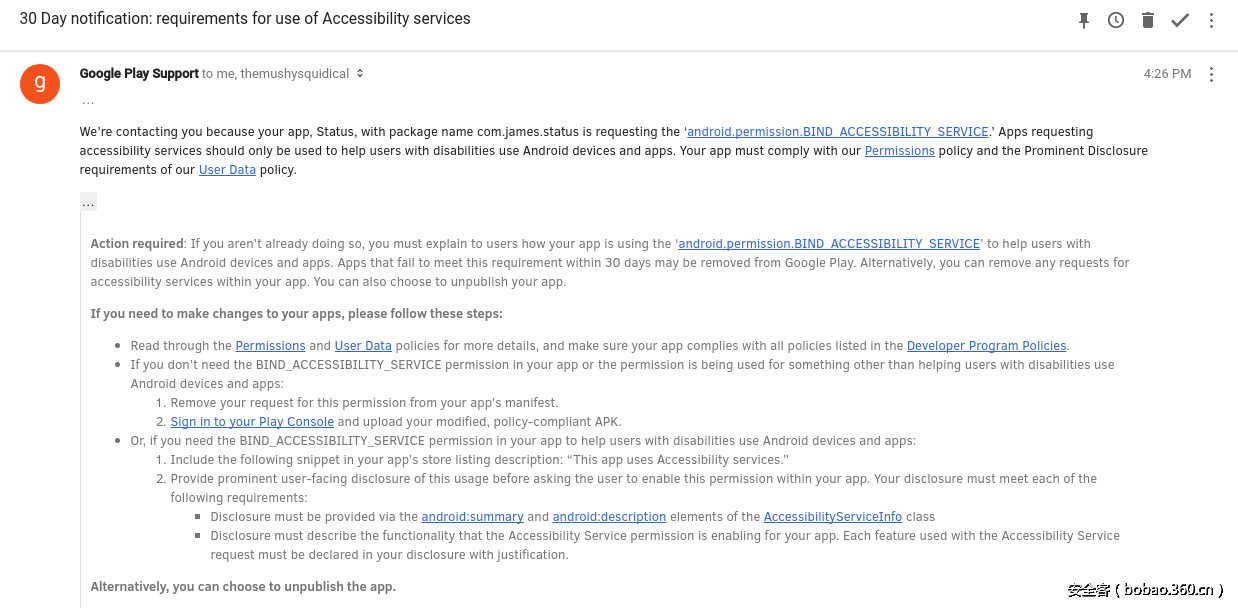
Google邮件通知安卓app开发者将那些滥用Accessibility(“无障碍”)服务的app从Play Store中移除
(在银行木马,移动勒索软件,点击欺诈机器人,广告软件以及任何其他种类的恶意app中经常出现无障碍服务的身影。多年来,这些恶意app想方设法诱导用户给恶意app授权无障碍服务。因为一旦用户授权,恶意app就可以在手机上后台任意下载执行恶意代码)
技术类:
漏洞聚焦:Foscam C1室内高清摄像机的多个漏洞(CVE-2017-2872连续编号至CVE-2017-2879)
(攻击者可利用这些漏洞在受影响的设备上实现远程代码执行,并将恶意固件镜像上传到设备,从而使攻击者完全控制设备。)
http://blog.talosintelligence.com/2017/11/foscam-multiple-vulns.html
之前的漏洞:
http://blog.talosintelligence.com/2017/06/foscam-vuln-details.html
以Emotet为例说一说识别C2服务器以及它们的网络拓扑结构的方法
https://www.malwaretech.com/2017/11/investigating-command-and-control-infrastructure-emotet.html
新的银行木马IcedID
https://www.bleepingcomputer.com/news/security/new-icedid-banking-trojan-discovered/
https://www.helpnetsecurity.com/2017/11/13/icedid-banking-trojan/
(C2: medicalciferol[.]com,MD5: 82d6e69df2277073d4aaacd6994ee033)
视频会议系统Polycom HDX的远程命令执行
https://staaldraad.github.io/2017/11/12/polycom-hdx-rce/
WordPress <= 4.8.2 SQL Injection POC
http://blog.vulspy.com/2017/11/09/Wordpress-4-8-2-SQL-Injection-POC/
Xlight FTP Server 3.8.8.5 – Buffer Overflow (PoC)
https://www.exploit-db.com/exploits/43135/
An unicode domain phishing generator for IDN Homograph Attack
https://github.com/UndeadSec/EvilURL
MazarBot 3.0木马
(IOC:
Distributed: hxxp://flashplayerupd.top/adobeflash.apk;
包名: com.rqojcxtxoh.kpxwqdygwl;
C&C: hxxp://5.188.231.154/index.php?action=command;
)
http://appscan.io/app-report.html?id=17fc1901ecb1dbc3eac089e578c5712aaab33a61
Oauth 2.0 redirection bypass cheat sheet
https://nbsriharsha.blogspot.rs/2016/04/oauth-20-redirection-bypass-cheat-sheet.html
修复了Host Header注入的WordPress插件
https://wordpress.org/plugins/host-header-injection-fix/
使用IDA Pro对进程注入恶意软件脱壳
https://www.youtube.com/watch?v=ScBB-Hi7NxQ
https://www.youtube.com/watch?v=kdNQhfgoQoU
Digging into radare2 for fun and profit