热点概要:穆斯林黑客攻击ISIS网站,公布2万名订阅者名单、卡巴斯基发布2017 Q3网络威胁的发展情况、PayPal子域存储型XSS、对Ordinypt恶意软件的分析报告、ARM虚拟机环境搭建教程(含虚拟机下载)、对垃圾邮件僵尸网络一探究竟、使用自动执行的宏或DDE生成并“感染”现有的Excel文件、Hijacking Digital Signatures
资讯类:
穆斯林黑客攻击ISIS网站,公布2万名订阅者名单
https://www.hackread.com/muslim-hacktivists-hack-isis-website-expose-subscribers-list/
卡巴斯基发布2017 Q3网络威胁的发展
https://securelist.com/it-threat-evolution-q3-2017-statistics/83131/
技术类:
PayPal子域存储型XSS
视频演示:https://www.youtube.com/watch?v=XwynfNOxIlI
对Ordinypt恶意软件的分析报告
http://29wspy.ru/reversing/Ordinypt/Ordinypt.pdf
Look Inside挑战的Writeup
https://0x00sec.org/t/writeup-look-inside/4310
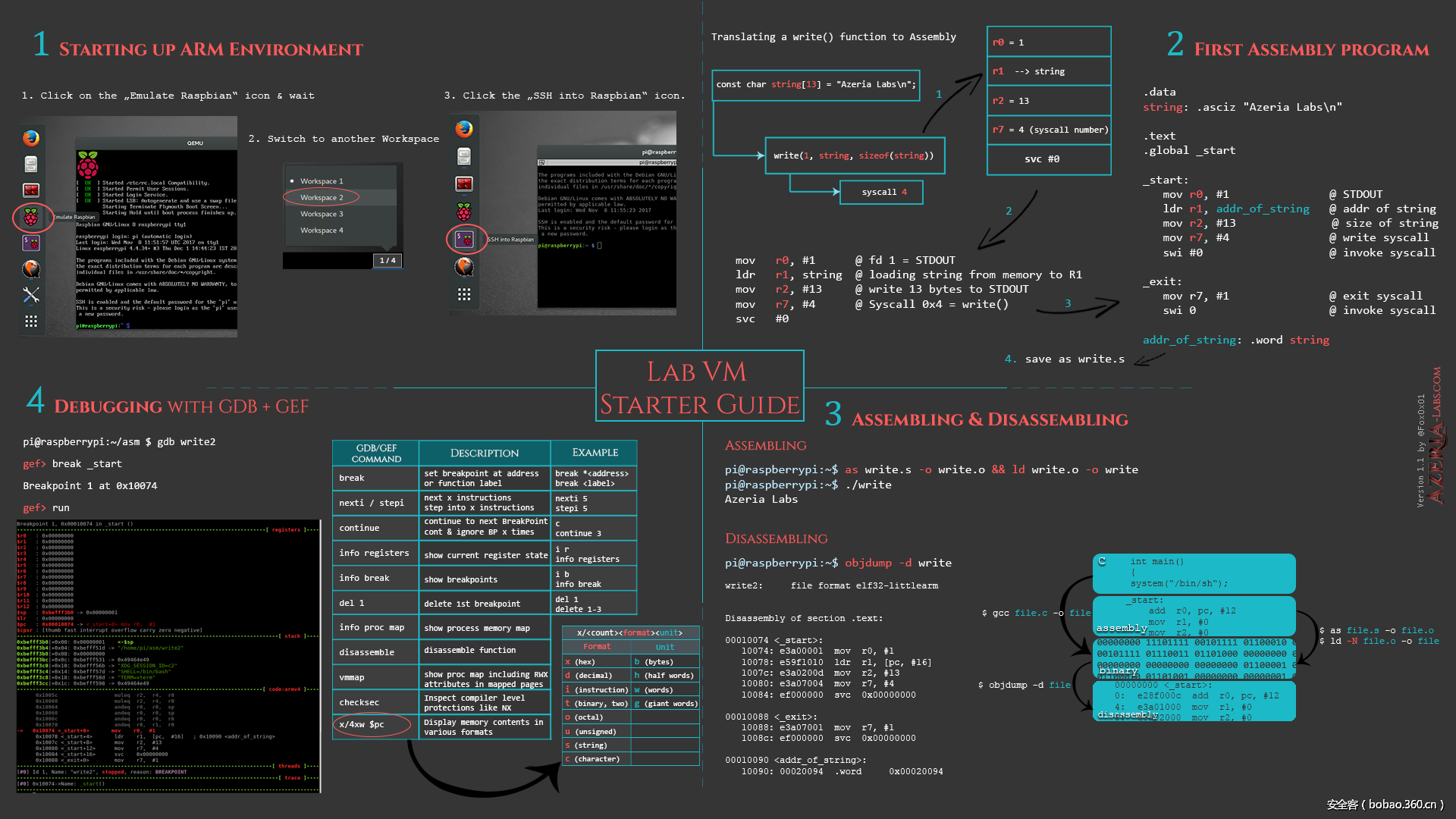
ARM虚拟机环境搭建教程(含虚拟机下载)
https://azeria-labs.com/arm-lab-vm/
Shed:.NET恶意软件运行时分析工具
http://antonioparata.blogspot.it/2017/11/shed-inspect-net-malware-like-sir.html
https://github.com/enkomio/shed
对垃圾邮件僵尸网络一探究竟
https://lokalhost.pl/txt/peering.into.spam.botnets.VirusBulletin2017.pdf
分享一些值得一用的BurpSuite插件
http://offsecbyautomation.com/Worthwhile-BurpSuite-Plugins/
使用自动执行的宏或DDE生成并“感染”现有的Excel文件
https://github.com/samratashok/nishang/blob/master/Client/Out-Excel.ps1
使用Autoruns:规避技巧以及对策
Googler:命令行使用Google的工具
(sudo add-apt-repository ppa:twodopeshaggy/jarun && sudo apt-get update && sudo apt-get install googler )
http://www.linuxandubuntu.com/home/googler-a-command-line-tool-to-search-google
在最新的Huawei Mate 9 Pro补丁上仅用NFC tag获得root权限
https://www.youtube.com/watch?v=UMrNQ1bnEBA
GlobeImposter 2.0勒索软件配置文件的提取脚本
https://gist.github.com/Demonslay335/8faaa57891318aa438db4bff10b347df
The Art of Exploiting Unconventional Use-after-free Bugs in Android Kernel
Hijacking Digital Signatures
https://pentestlab.blog/2017/11/06/hijacking-digital-signatures/
x86 userland minimal examples
https://github.com/cirosantilli/x86-assembly-cheat
x86 Bare Metal Examples
https://github.com/cirosantilli/x86-bare-metal-examples
Destroying the Reddit Lovense Remote Vuln Conspiracy
https://internetofdon.gs/2017/11/11/destroying-the-reddit-lovense-remote-vuln-conspiracy/